Here Is Njalla's Take on the Domain Hijack
Someone stole the domain darknetlive.com and used it to share phishing links. Njalla, the “domain name registration service” we used at the time of the breach, published a blog post that answered some of the questions asked by readers of this site.
Here is what they wrote:
A lot of people are public about their usage of Njalla. We however find that it’s their prerogative to decide if they want to acknowledge our relationship. We’re like that secret partner that’s ok with being a secret, maybe kept on the side or maybe just because real intimacy is the business of just the involved parties. That’s why we rarely openly talk about dealings with specific domain names that are registered through us.
However, the past few days there has been a quite unique attack that has affected some domains registered through us. The registrants of those have been vocal about their relationship with us, and we’ve worked together in trying to rectify the problem. For transparency and to learn from this situation we decided to write up a post about what happened and how we’re making sure this will not happen again.
To explain we need to explain a bit how Njalla works. The main difference between us and many other registrars is that we’re the legal owner of domains. Many other registrars offer a service of being a proxy in between, but the regulations mean that they will hand over the user data whenever there’s any sort of inquiry. Some registries (TLDs) even require this data to also be sent to them at registrations. Taking the legal ownership means that we are also more liable than what other registrars are — and want to be, which is why we’re unique in how we operate.
This is also a bit problematic though. First of all the end registrant needs to trust us that we will not run away with their domains. After this many years in operation and a flawless track record, the trust seems to be established (and we’re happy for that trust). It also means we’re harsher than other registrars against phishing, scams and we operate quickly to resolve cases like that. For us this is a win-win since we also want a cleaner internet - freedom of speech doesn’t mean the right to spread malware. We protect those that need it, not those that want to abuse it.
Another problem is that we many times also need a go-between ourselves. The regulations of most TLDs (such as .com .net .org etc) are very often that the registrar is not allowed to register end-registrant domains for themselves. So we have partnered up with other registrars to register domains through them, so we’re the end customer. This means that they only know our information as the registrant, and we work closely together to mitigate any potential issues that arise (such as the aforementioned phishing situations for instance).
A few days ago, one of our partners (Tucows) was however the victim of a phishing attack themselves. They received a court order (including a gag order) to hand over a set of domains, where some were registered through Njalla (and others weren’t). Tucows receives quite a lot of these court orders and got tricked by them. We haven’t gotten all of the details with them on exactly how the full attack was done, but we’ve asked for clarifications. We have been promised that Tucows has strongly improved their operations for how to deal with future court orders.
So this was a directed attack against specific domains, through a specific partner, with a gag order. Tucows believed they were not allowed to inform us, and thus didn’t (and therefore we couldn’t inform our registrants). This means that no data was leaked, but it did lead to the domains being hijacked. These domains were later updated with new content which led to phishing attacks on their user base, which we are extremely upset about.
These situations are unfortunately more or less out of our hands. We have selected partners that agree on our values (like privacy and open internet) and that can also handle the legal aspects of working with a unique niche operation like ours. A major problem with domains is however the centralized operations that it’s built upon. We have one single instance called ICANN that controls 90%+ of the TLDs that exist (essentially all TLDs that are not governed by a territory), and then the few registrars that have volume enough to make direct agreements with these TLDs. This is one of the things that we started Njalla to combat - in the long term we’re working against this centralization and wanting to get volume enough to be a voice of reason within this industry. We believe that if more registrars operated the way we do - and would take the same effort to fight court orders as we do - this attack would not have been possible.
And speaking of this industry, and to continue with the story of the hijacked domains: the domains were transferred internally at Tucows to their compliance department and then handed over to the attacker, who then immediately transferred these domains to other registrars. In our case, it was Epik and Namecheap. Epik is a registrar we do not like for political reasons but credit due where credit is due, they handed back the domain that was transferred to them as soon as they were informed about what had happened.
I personally like Epik’s embrace of free speech. Njalla is favorable to free-ish speech as well. I am indeed fortunate that Epik responded to my complaint in just hours. Before the case had closed, Epik locked the domain to prevent further changes. Their handling of the case was exceptional considering that darknetlive.com is registered at Tucows through Njalla.
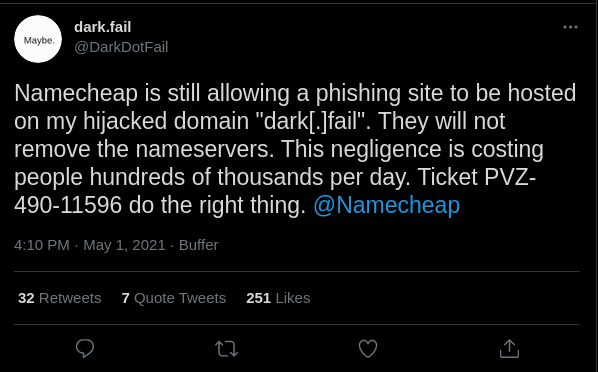
Hours before Epik locked the domain, the attacker tried to auction it off. | DarkDotFail
Dark.fail has not been as fortunate, as described in the paragraph below. The dark.fail onion address is still owned by the correct owner but Namecheap seemingly lacks a sense of urgency when it comes to returning the domain to dark.fail.
Namecheap on the other hand, one of the largest registrars in the world, decided not to yet. Even though the rules are quite clear in these cases. They have also decided to not disable the domain usage. This means the phishing attacks on the domain in question are still ongoing even though Namecheap has been informed multiple times, including the fact that the court order that they justify the transfer with was a faked one. We know that Namecheap and Tucows have some animosity between them after a previous feud but hope that they will not let third-parties suffer because of it. It’s extremely concerning that a company like Namecheap does not take this situation more seriously and swiftly returns the domain to the registrant (and meanwhile disables the usage of the domain).
After all of this is done, we’re going to have a debriefing with our partners to understand more about what exactly happened and we’ve already offered our expertise where it might be helpful.
Thanks to everybody, including @darkdotfail, @notdan, and others, who helped attract attention to this issue. If not for the people lobbying on the behalf of us, I am not so sure we would see the domain again.
With that said, we are supposed to take Tucows at their word when they claim they “strongly improved their operations for how to deal with future court orders.”