Signal Desktop Update Patches a Privilege Elevation Vulnerability
Rich Mirch, a security researcher and penetration tester, discovered the vulnerability and wrote about on his personal blog after Signal released an update for Windows on December 17, 2019. The update is available here.
Signal Desktop v1.29 on Windows is vulnerable to an elevation of privilege vulnerability. During the startup the application will execute the c:\node_modules\.bin\wmic.exe binary if it exists. By default on Windows, low privileged users have the privilege to create folders under root level drives. A low privileged user can create a malicious wmic.exe which will be executed every time Signal Desktop starts by any user of the system. The malicious binary is executed in the background without the users knowledge. This is an example of horizontal privilege escalation.
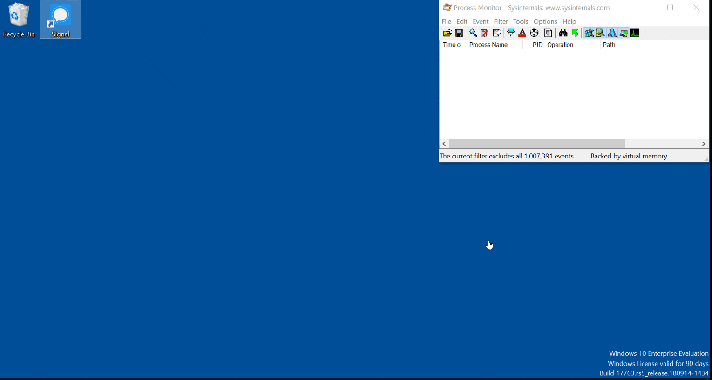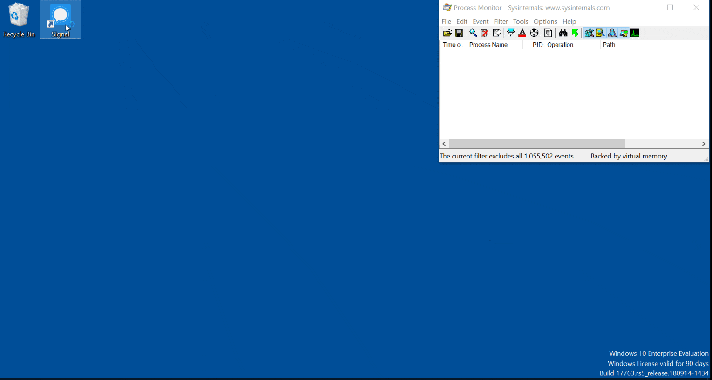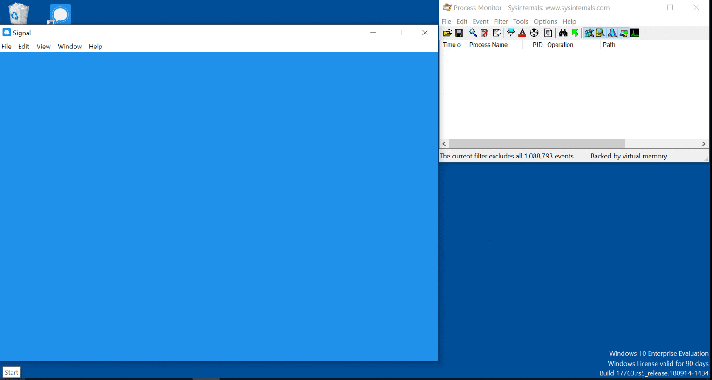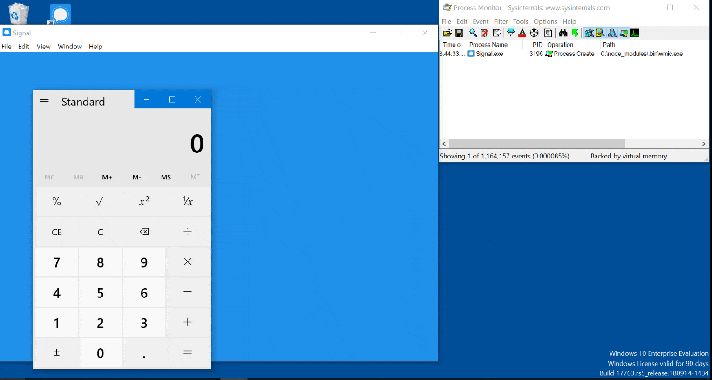
A POC Provided by Mirch
The vulnerability has been patched in v1.29.1 in commit 2da39c which was released 12/17/2019. Kudos to the Signal security team for fixing in less than two weeks! Unfortunately, at this time the they do not feel this warrants an advisory or CVE so the vulnerability was silently fixed.
A copy of the vulnerable version is available here: https://updates.signal.org/desktop/signal-desktop-win-1.29.0.exe.
Read the complete post on Mirch’s blog, blog.mirch.io.