On April 4th, the FBI, in cooperation with several international law enforcement agencies, seized the domains of Genesis Market. The service was shut down, and its clearnet infrastructure seized. This operation was called "Cookie Monster."
Simultaneous actions were also carried out across the globe against the users of this platform, resulting in 119 arrests, 208 property searches and 97 knock- and-talk measures.
Not so long after the final seizure, the administrator's account of the Genesis market posted on two Russian cybercrime forums, Exploit.in and XSS.is, announcing that they will be using the old Tor domain going forward. It can be assumed that the platform admin have not been caught yet, however, this could also be a honeypot.
Genesis Market was a marketplace where cybercriminals offered login credentials for sale for numerous different services. The offers related to both corporate and consumer accounts. These included social networks such as Facebook, Twitter, LinkedIn or Reddit and also streaming services such as Netflix or Spotify. Accounts from Gmail, WordPress, PayPal, Amazon, Cloudflare, Zoom or eBay could also be purchased there.
Most of these data were acquired through malware or account takeovers attacks.
With special browser plugins, Genesis Market made it easy for users to access the compromised accounts, referred to as "bots"; with just a few clicks the acquired credentials were imported directly into the web browser, a buyer could thus assume the digital identity of another person. Cookies, fingerprints, saved logins or autofill form data; all there. This allowed the criminals to access the victim's account without triggering any of the security measures from the platform the account was on.
The price per bot would range from as little as USD 0.70 up to several hundreds of dollars depending on the amount and nature of the stolen data. The most expensive would contain financial information allowing access to online banking accounts.
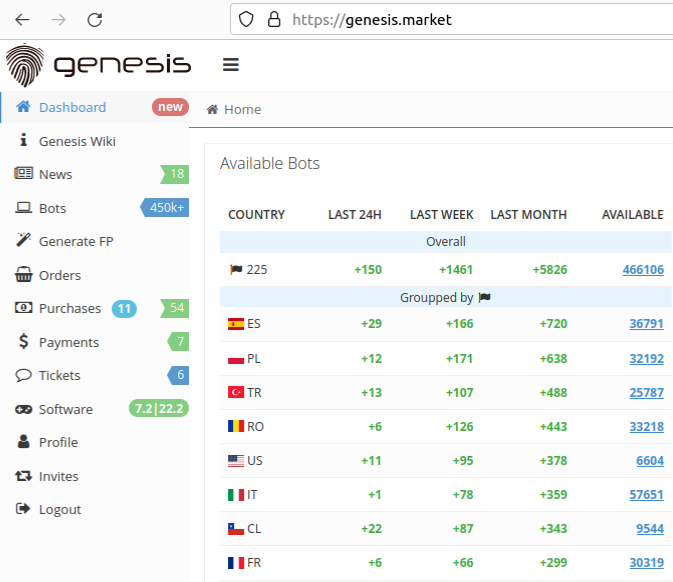
It was considered one of the biggest criminal facilitators, with over 1.5 million bot listings totaling over 2 million identities at the time of its takedown.
Unlike other criminal marketplaces, Genesis Market was also accessible on the open web, in addition to their .onion domain. Their .onion domains appears to be intact.
The US Department of Justice also released a document detailing the investigation, alleging that law enforcement officers managed to gain access to the backend of the site, in December 2020, as well as to the data of 59,000 users, including passwords, email addresses and cryptocurrency wallets and logins in Jabber.
Key points from the warrant:
- In September 2018 the FBI purchased 115 bots from the market and paid in Bitcoin.
- Tracing the Bitcoin led to hosting services providers located in the US.
- Information acquired from the hosting providers led to the market's backend server.
- In December 2020, the investigators obtained a "forensic image" of the server.
- Shortly after, Genesis admins changed hosting providers and moved their servers out of the US.
- The investigators once again gained access to the database associated with the markets server in May 2022.
- In April 2023 the investigators seized 11 clearnet domains associated with the market.
- At the same time, LEAs in 17 countries executed search warrants for market's most 'prolific' users.
- OFAC believes Genesis Market admins are located in Russia.
The United States Treasury Department also imposed sanctions against Genesis Market domains.
The Dutch computer security firm Computest worked with Trellix and the Dutch Police to analyze the Genesis Market malware here.
Add bitcoin in to your opsec equation and you will always fail. When will they learn?