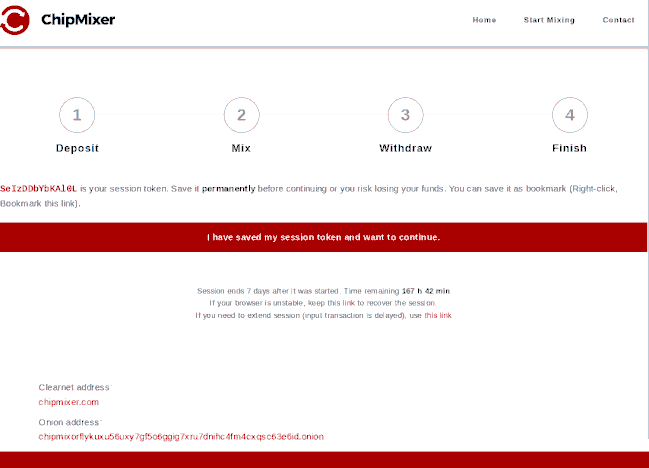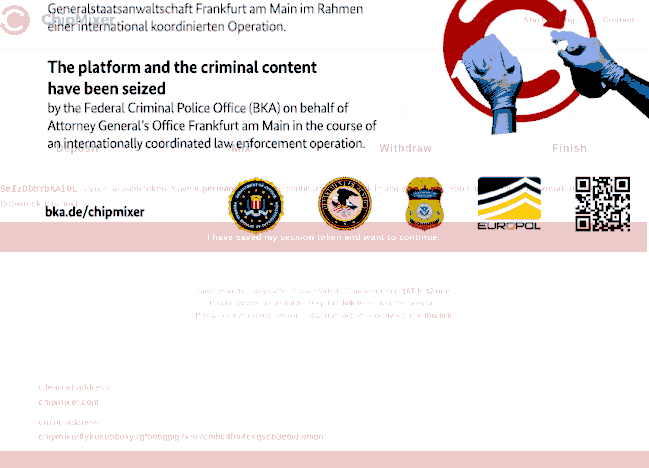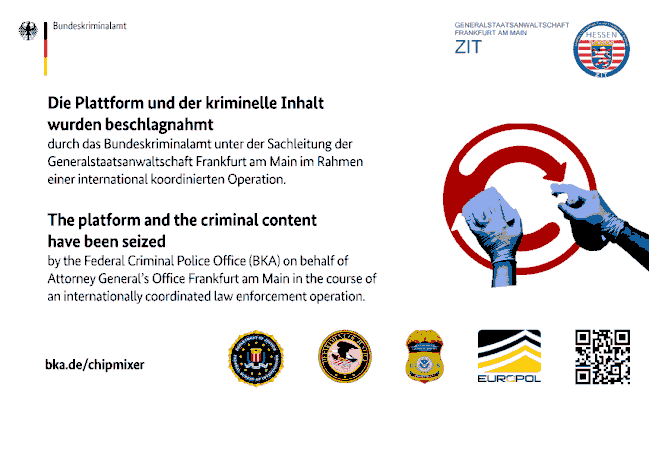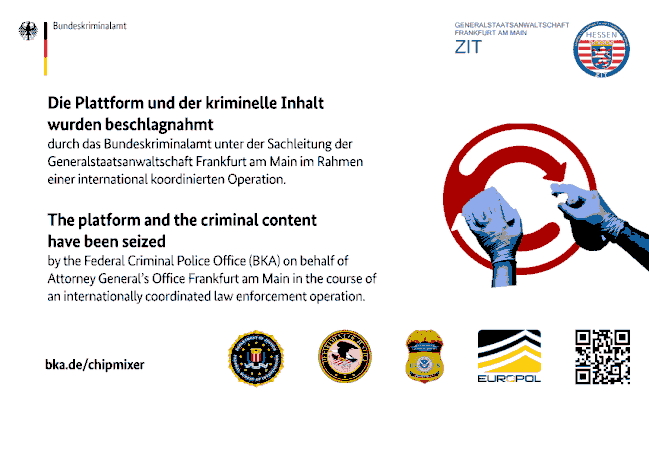
German and US authorities, supported by Europol, have seized ChipMixer, an unlicensed cryptocurrency mixer well-known in the cybercriminal underworld. The investigation was also supported by Belgium, Poland and Switzerland. On 15 March, national authorities took down the infrastructure for its alleged involvement in money laundering activities and seized four servers, about 1909.4 Bitcoins in 55 transactions (approx. EUR 44.2 million) and 7 TB of data.
The contents of 7 TB of data found is not specified. This data could be anything from cryptocurrency nodes, to backups containing mix data and private keys.
Europol said ChipMixer helped hide the trail of digital money for online drug traffickers, Russian military hackers and North Korean cybercriminals. In doing so, the mixer facilitated money laundering of 152,000 Bitcoins.
The Frankfurt General Prosecutor's Office, Central Office for Combating Cybercrime (ZIT), and the German Federal Criminal Police Office (BKA) were involved in the operation. In a press release, the BKA said they seized ChipMixer's server infrastructure located in Germany on Wednesday. The U.S. authorities seized two web domains that directed visitors to ChipMixer and a GitHub account that contained project code. Both their Tor and clearnet website now show a seizure notice.
After the seizure, authorities left "easter eggs" around ChipMixer's onion site. The session token, used for tracking a mix, reads "SeIzDDbYbKAl0L", and the footer text "Want to earn an honest living in crypto? Visit our career page!" directs you to work for the German Federal Criminal Police Office.
On November 23, 2021, ChipMixer's clearnet address, which was used solely to direct people to their Tor site, was seized. The FBI served a federal search warrant to DigitalOcean for chipmixer.com:
FBI analysis of this server image revealed that it contained minimal information about the administrators, customers, or operations of ChipMixer, and it pointed traffic to a ChipMixer Tor server.
Authorities didn't specify how they located the onion site. Although, both the clearnet and onion sites where hosted with Hetzner. The FBI's vague statement about locating the onion server:
Through the course of the investigation, and working in partnership with foreign law enforcement, the FBI identified that another ChipMixer server resolved to IP address 138.201.227.85, hereinafter the “V3 Server.” Open-source research conducted on IP address 138.201.227.85 revealed the IP address resolved to Hetzner Online GmbH (Hetzner) in Germany.
How Minh Quoc Nguyen was Identified
The US Justice (DOJ) announced it had indicted Minh Quoc Nguyen, a Vietnamese national from Hanoi. The alleged 49-year-old owner is charged with commercial money laundering, operating an unlicensed money transfer business, and also identity theft in connection with the operation of ChipMixer. He is currently wanted by the FBI.
Beginning in and around August 2017, Nguyen allegedly created and operated the online infrastructure used by ChipMixer. In addition, it's said that he advertised ChipMixer's services online, registered domain names, procured hosting services, and paid for them.
He disguised his identity by using other identities, pseudonyms, and email providers.
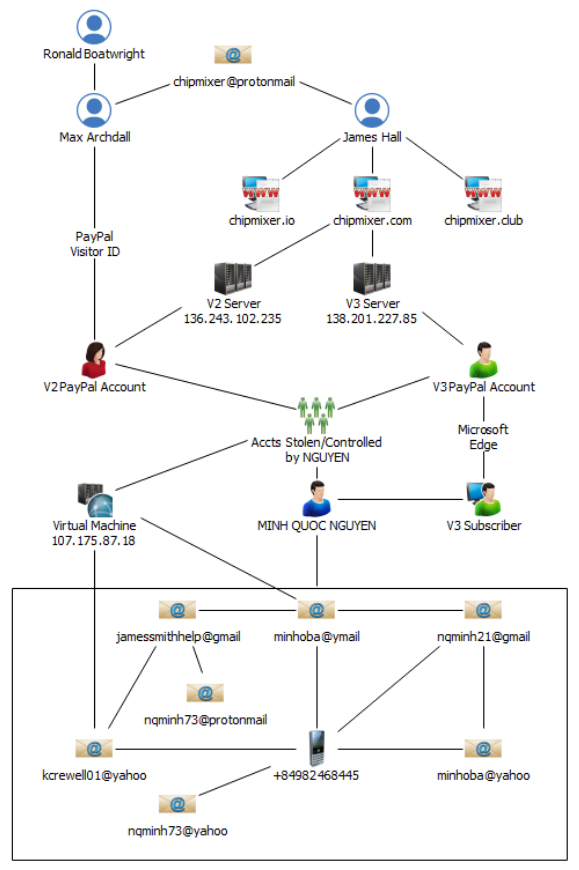
Nguyen was linked to ChipMixer in multiple ways. He used many clearnet email providers and indirectly used his own PayPal account to pay for the servers.
PayPal accounts linked to the account that was paying for the servers:
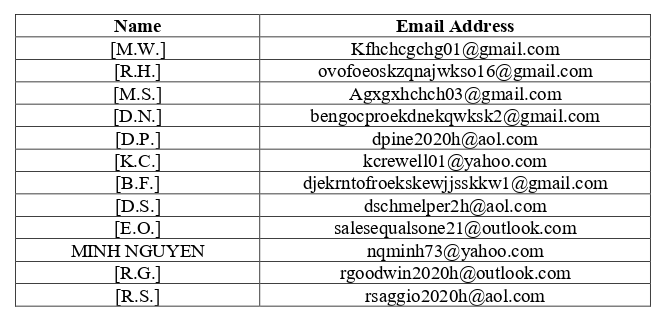
Open-source research conducted on the above accounts revealed the identifying information associated with the accounts are primarily United States-based persons, approximately 60-70 years old, except for the account associated with MINH NGUYEN. Commercial database research revealed that some of these persons are deceased.
According to PayPal records for the V3 PayPal Account (the account paying for the server), on December 27, 2022, there was a credit card payment received from MINH NGUYEN, email address nqminh73@yahoo.com for $150.00 with the comment “Thanks.”
The FBI found transactions with 70 different PayPal accounts using ProtonMail addresses when they dug deeper into the PayPal accounts above. They then submitted international records requests for subscriber data for these ProtonMail accounts. Of these accounts, 24 of them listed jamessmithhelp@gmail.com as a recovery email address and nine listed minhoba@ymail.com as a recovery email address.
Records from Google for the account jamessmithhelp@gmail.com revealed location history data. From September 2016 through March 2022, there were 149,027 data points associated to the account that resolved in and around Ha Noi, Vietnam. The location history data is a combination of different sources to include cell, GPS, and Wi-Fi, showing that NGUYEN was physically in Vietnam during these data points.

Search warrant returns from Google for jamessmithhelp@gmail.com revealed searches by Nguyen for ways to buy personally identifiable information. The following Google searches were conducted:
- “where to search for ssn free by name”
- “selling ssn dob”
- “ssn dob shop”
- “ssn number generator”
Binance provided records relating to jamessmithhelp@gmail.com, which revealed an account registered with Nguyen's own name and ID. Transaction data from Binance showed Nguyen cashing out using Remitano, a P2P Bitcoin marketplace, where he also used his ID.
His anonymous email accounts ended up being linked to accounts from Dropbox, Apple, BlackHatWorld, ResearchGate, Reddit, Microsoft, Google, PayPal, BitcoinTalk, ProtonMail, LinkedIn, Twitter and Investing.com.
About Nguyen
Nguyen often expressed his views stating that "Money laundering is a crime made-up by governments that spy on their citizens" and advised people "not to use AML/KYC services". Eventually he became victim of his own words as he repeatedly used Binance and PayPal which lead to his identity.
If currently residing in Vietnam, Mr. Nguyen might be a lucky guy. Vietnam does not extradite its citizens and last time the US tried to apprehend a Vietnamese cyber criminal, they went as far as luring him to Guam to capture him. If otherwise convicted, he faces a maximum sentence of 40 years in prison.
Some people think that Nguyen is not the mastermind behind ChipMixer, due to his "basic training in cryptographic engineering" and mistakes in concealing his identity.
Did anyone ever explain OPSEC to this guy?