Feds Seized the Carding Shop “WT1SHOP”
U.S. law enforcement seized four domains associated with the WT1SHOP carding marketplace.
Law enforcement agencies in the United States seized the domains “wt1shop.net,” “wt1store.cc,” “wt1store.com,” and “wt1store.net.” Authorities in Portugal shut down the Wt1Store server. A criminal complaint charging the alleged operator of the website with access device fraud has been unsealed in the District of Maryland.
In 2020, law enforcement learned that WT1SHOP was hosted by a Ukrainian hosting provider at a data center in the Netherlands. Records from the hosting provider indicated that someone with a fake name using “email address 2” had paid for the WT1SHOP servers. After 2020, the site administrator moved the market to a data center in Portugal.
A screenshot of a WT1SHOP banner
Dutch law enforcement obtained an image of the server hosting WT1SHOP.
“When the image was taken, the server was not taken offline and thus, the data was captured live, allowing files to remain open and applications to run in memory. As a result, the database was found to contain some incomplete and/or corrupt records.”
The server image included a database, historical information about WT1SHOP vendors, and transaction information. The database contained login credentials advertised and sold by vendors on the marketplace.
As of June 6, 2020, there were approximately 60,823 registered users on WT1SHOP, including 91 sellers and two administrators. Vendors on the marketplace had sold at least 2.4 million logins for a total of $4,038,889.
A summary of the types of credentials sold on the market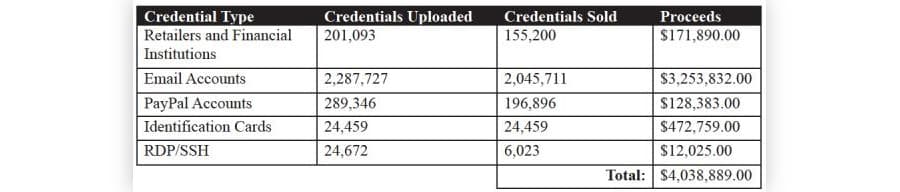
From July 15, 2015, to June 6, 2020, vendors on the marketplace withdrew approximately $621,400.
In January 2020, a confidential source in Maryland conducted an undercover purchase of ten Marriott login credentials; ten American Express credit card accounts for individuals with Maryland
addresses; and two Maryland driver’s licenses. A review of the site’s database accurately reflected the source’s purchase.
In December 2021, a second confidential source conducted an undercover purchase from the site. The source purchased three U.S. passports with a Maryland place of birth; ten PII for individuals residing
in Maryland; five BB&T bank login credentials; and five Marriott login credentials.
“During the transactions, CHS 1 and CHS 2 (collectively, “CHSes”) transmitted payment to WT1SHOP via Bitcoin through a Bitcoin exchange (“Bitcoin Exchange”). The Bitcoin Exchange webpage contained the relevant transaction details for the CHSes to complete the transaction and add virtual currency to their accounts on the WT1SHOP website. Once the transactions were finalized, the CHSes’ accounts on WT1SHOP showed a credit balance, which was used to provide payment to WT1SHOP for the purchases. For each purchase made on the WT1SHOP website, the amount was subtracted from the balance on the CHSes’ respective accounts. Of note, the Bitcoin Exchange web page for CHS 1’s transaction included a Payment ID ending in ZI4U and an email address of the virtual currency account associated with WT1SHOP, Email Address 3.”
In a separate search in November 2017, law enforcement learned that the domains wt1shop.org and wt1shop.net were registered using Email Address 1. Investigators obtained records from Google with copies of emails received by Email Address 1. The emails indicated that the user had an account with the Bitcoin Exchange.
Through an MLAT request to the Republic of Estonia, the Bitcoin Exchange provided records regarding the payment account that received the payments from the confidential sources and accounts associated with Email Address 1 and Email Address 3.
These records included registration information, I.P. address logs, and transactional records.
“According to the records provided by the Republic of Estonia, Bitcoin Exchange account with User ID 2705837 and connected to Email Address 3 (“Bitcoin Exchange 1”) was registered in a Russian name—Individual 1. The account was registered using Email Address 4.
According to records provided by Cloudflare for the WT1SHOP domains wt1store.org, wt1shop.net, wt1store.net, wt1store.com, and wt1store.cc, the associated Cloudflare account was registered using Email Address 4. […] The Bitcoin Exchange 1 account used the Public Name “wt” and was registered with the public email address Email Address 3, the email
address is shown on the Bitcoin Exchange webpage connected to WT1SHOP.”
“The Bitcoin Exchange also provided subscriber information and details regarding the account connected to Email Address 1, including the I.P. addresses used to access the account. Bitcoin Exchange User ID 482927 (“Bitcoin Exchange 2”) was registered to Email Address 1 with a username of “teamteam” and Public Name of “wt”—the same Public Name used for Bitcoin Exchange 1. Bitcoin Exchange 1 and Bitcoin Exchange 2 were accessed from the same I.P. address (89.187.50.10) on the same days. For example, Bitcoin Exchange 2 logged into the account on 11/05/2019, 01:23:05 UTC from the I.P. address 89.187.50.10 and within a minute (01:24:05), the same I.P. address logged into Bitcoin Exchange 1, indicating that these two Coin Payments accounts
are controlled by the same individual. A review of the Email Address 1 account showed that the account received emails from the Bitcoin Exchange, indicating that a Bitcoin Exchange account may have been registered using Email Address 1.”
A picture of the login page for WT1SHOP
During a review of Email Address 1, investigators learned that the account holder had purchased multiple travel tickets using the name “Nicolai Colesnicov.” One of these tickets included a Moldovan passport number ending in 8169.
Finally, the I.P. addresses that accessed Email Address 1 and Email Address 2 were the same I.P. addresses that had accessed the “admin” account in the WT1SHOP database.
On September 6, the United States Attorney for the District of Maryland Erek L. Barron, announced the seizure of some of the WT1SHOP domains and the criminal complaint accusing the defendant of operating the market.
“If convicted, Colesnicov faces a maximum sentence of 10 years in federal prison for conspiracy and trafficking in unauthorized access devices. Actual sentences for federal crimes are typically less than the maximum penalties. A federal district court judge will determine any sentence after taking into account the U.S. Sentencing Guidelines and other statutory factors. "
Website Selling Stolen Login Credentials and Other Personally Identifying Information is Seized and Its Operator Faces Federal Charges for Conspiracy and Trafficking in Unauthorized Access Devices | www.justice.gov, archive.is, archive.org