Paris: Versus Market Exploit “is Real”
The Versus Market exploit is legitimate, Paris claimed.
A user on Dread (/u/threesixty) hacked Versus Market “in a time span of about 2 hours,” according to a post on the Versus subdread. “Please remove security driven from your website title. You are not security driven.”
threesixty generated little traction with his brand new account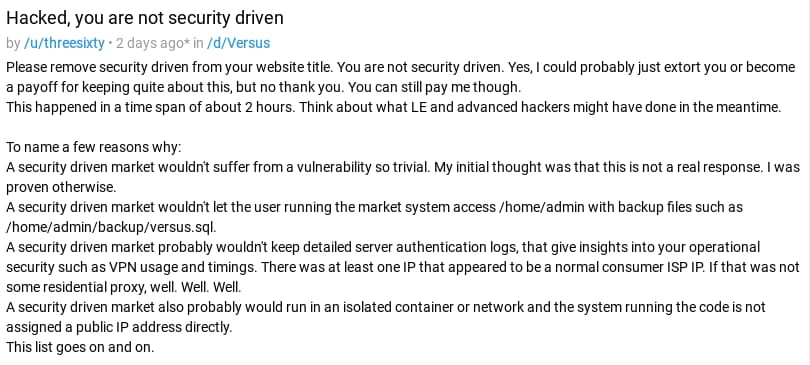
The user who had discovered the vulnerability, /u/threesixty, contacted DeSnake, the administrator of AlphaBay, about “the security issues on Versus.” According to DeSnake’s posts on Dread about the incident, he initially assumed threesixty’s post contained FUD. DeSnake and threesixty then worked together “to get even more proof on top of what he had recovered initially.”
A “meaningless excerpt from the file,” posted by threesixty as a form of proof for Versus staff. It is not a form of proof for those of us without access to Versus:
--
-- Table structure for table `crons`
--
DROP TABLE IF EXISTS `crons`;
/*!40101 SET @saved_cs_client = @@character_set_client */;
/*!40101 SET character_set_client = utf8 */;
CREATE TABLE `crons` (
`id` int(10) unsigned NOT NULL AUTO_INCREMENT,
`created` timestamp NOT NULL DEFAULT current_timestamp(),
`last_edit` timestamp NOT NULL DEFAULT current_timestamp() ON UPDATE current_timestamp(),
`next_run` timestamp NOT NULL DEFAULT '0000-00-00 00:00:00',
`interval` int(10) unsigned NOT NULL,
`cron` text NOT NULL,
`took` bigint(20) NOT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=14 DEFAULT CHARSET=utf8mb4;
/*!40101 SET character_set_client = @saved_cs_client */;
--
-- Dumping data for table `crons`
--
LOCK TABLES `crons` WRITE;
/*!40000 ALTER TABLE `crons` DISABLE KEYS */;
INSERT INTO `crons` VALUES (1,'2019-12-03 09:56:24','2021-10-16 17:24:18','2021-10-16 17:25:18',60,'check_invoices',7238),(2,'2019-12-03 09:56:14','2021-10-16 17:24:03','2021-10-16 17:25:03',60,'get_rates',219)...
DeSnake described the impact of their work as a “complete takeover. Database, files, cryptocurrency wallets (of course those that have used multisig are okay either way), real IP exposed etc. Complete pwn.”
Versus hacked for 3rd time or why security must be a priority for DNM admins
The hyperlinks have been removed to prevent you know, the thing.
DeSnake:
Disclaimer: Before I begin with the post I would like to point out that I do not have anything against /u/WilliamGibson himself. Yes I do not think security (getting hacked 3 times) and stability (offline almost all the time during DDoS) is on point for their status as a marketplace even more so 3 years down the line. Yes their inability to get their Staff issues/communication spills over the business and the posts from customers speaks for that. However at the very least they kept going and were providing a platform for people to trade.
I was contacted around a day ago by the hacker /u/threesixty about the security issues on Versus. As with everything I take it with a cup full of salt before I do my own verification. I took a look at his profile and of course it was a new one which led me even further to believe this to be FUD. He had created a post on Versus subdread (dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad.onion/post/e408c16ab482106c4eea)/ which got suprisingly little attention for the details that it was outlining and claiming.
I decided to ask him for further details and in an encrypted PGP message he provided an interesting amount of information. Now anyone could have created that information so the only way to verify it was to test myself. I was almost certain it had been patched by Versus… but even after the post threesixty had done the vulnerability was still sitting there plain as day allowing anyone to browse through the system and potentially escalate to full control over the server.
Together with the good-willed hacker 360, we were able to get even more proof on top what he had recovered initially that indeed it is the real server of Versus. All proof was provided to Paris right before putting this post up.
The Vulnerability
Testing the vulnerability was straightforward and as threesixty said a textbook one. There was no complexity in it or discovering it. How no one has reported it or fixed in 3 years I or him do not understand. Complete props go to him for finding it.
The Impact
Complete takeover. Database, files, cryptocurrency wallets (of course those that have used multisig are okay either way), real IP exposed etc. Complete pwn.
From threesixties (and mine) side nothing has been taken or modified in any shape or form. Only information was downloaded such as databases and files (including system ones to prove the existence) which would allow us to prove the vulnerability exists to other high ranking people like /u/Paris . Cryptocurrency wallets were never touched.
Given the issues with security that are now happening for the 3rd time in the markets history, Staff problems also affect Versus. I have no doubt that affects the security and maintenance of the marketplace. Staff are a core part of the marketplace without Staff administrators are nothing and vice versa. So for all of you marketplace admins make sure your Staff are well, financially and in other ways. When you are an employer it is your duty to ensure you create a good environment for individual employees to thrive and grow both professionally and personally.
Witchman05 himself said in this thread about Versus vendor issues, quote dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad.onion/post/e83da76a7c5f41e2f844)/#c-f13009c91041cbb306
I do know that Huxley, Poe, Gibson and Rowling have had some differences in opinion that came to a head about two weeks ago, and they’re probably still kind of simmering about that. I won’t go into detail, because that’s their business, but just saying, you’re probably not going to get an instant reply on this thread. There were a lot of factors, a lot of… underlying issues, a lot of kind of hurtful things were said, and it was honestly kind of ugly. I’ve been talking with all of them, seeing it from all sides, and while I’m honestly kind of hesitant to pick sides on that whole mess, considering I don’t have any sort of actual bond to the market itself anymore, I will say some things definitely could stand to have a bit of a shake-up in the process it’s been handled with.
Of course, I could be wrong. These guys that I’ve known for almost a decade could have decided to go completely irrational at the drop of a hat, burning not only these names but also their entire reputation for the rest of their careers on the Darknet.
My point is, be careful, all.
What I am trying to get to here is it all starts within. Bad Staff management leads to poor handling of tickets, lack of care for either customers or vendors, lack of any upkeep on servers and network and so on. As a marketplace putting up a patch is not enough e.g. restarting your services because they went down due to DDoS. Ask yourself why did they go down what is the core issue, it is all in the logs. That is how you solve the core of the problems not treat the aftermath with painkillers figuretively speaking. Not everyone has this way of thinking and that is fine but as a marketplace, a reputable one, it is your duty to have your shit in order.
I would also not be surprised that some of the ‘phishing’ of high ranking vendors that has happened had actually been hacked accounts from the database. Lots of reputable vendors got ‘phished’ with no clear explanation in sight. I am assuming another hacker has the Versus database as well and knows about this or other vulnerabilities and has abused their access.
In spirit of full disclosure currently Versus markets backend seem to be giving a white screen of death which may or not be related to the thinkering myself and /u/threesixty had been doing. That white screen has happened before which would mean we have not caused it or… someone else has had access to files and databases like we did and has abused it to DoS the backend into submission. If it had been a result of our testing we apologize.
We hope to have a fruitful conversation about security on marketplaces especially on established ones. Since day one my goal with AlphaBay was security followed by stability and usability and in the era of takedowns, DDoS (which further exposes your infrastructure as a marketplace) and rinse and repeat scams like those of groups like lovelace, administrators can not allow themselves not to test every single user input and sanitize it.
Further how an active Web Application Firewall (WAF) is not present on Versus is also beyond me. A lot of features of ‘security’ seem to be missing by a ‘security-driven marketplace’ like Versus claims to be. Admins should not be slacking when it comes to the security of their customers who are both buyers and vendors. The results are known what happens when you let go and do not follow the security guideliness. Security is not a product, it is a never-ending process.
Both threesixty and myself have the best intentions. That is why we did not leak the database or stole any coins. For me personally, 3 times is too much of anything but as with everything we should at least be grateful for what we have first and then work on improving it second.
Thank you.
Dread: dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad.onion/post/81fac8c141c9fc519b9f
Paris
Paris, the co-administrator of Dread, responded in the comment section of DeSnake’s post, claiming that he had verified the exploit.
Paris:
/u/DeSnake has provided me the exploit and rational. I have personally verified it.
IT IS REAL.
The exploit is extremely simple but compromising. It allows for full access to the underlining file system on the server. This include information within the /etc/ directory as well as wallet directories. It is a full information compromise of the system. Everything to the server’s IP address, to the backup of the database in the admin home folder, to the wallet files themselves. I am able to traverse nearly the entire file system with web server level access. There is no jail, WAF, and minimal care to limit the information disclosure in the event of a web server compromise. I am able to view the history of IP addresses which have previously accessed the server.
This is a major compromise and it is very easy to find and pull off. Even a simple scriptkitty that is running a web server tester will find this exploit. /u/WilliamGibson I will be passing this information over to you. This shouldn’t be a problem with even the most basic jailing practices on the web server layer.
Until such time as this is fixed nobody should use Versus. I can’t say that enough. This entire server is probably compromised already by law enforcement and being monitored. It is a total compromise and is without a doubt one of the worse outcomes to a simple security exploit I have seen in a very long time.
Signed Copy
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA256
/u/DeSnake has provided me the exploit and rational. I have personally verified it.
IT IS REAL.
The exploit is extremely simple but compromising. It allows for full access to the underlining file system on the server. This include information within the /etc/ directory as well as wallet directories. It is a full information compromise of the system. Everything to the server's IP address, to the backup of the database in the admin home folder, to the wallet files themselves. I am able to traverse nearly the entire file system with web server level access. There is no jail, WAF, and minimal care to limit the information disclosure in the event of a web server compromise. I am able to view the history of IP addresses which have previously accessed the server.
This is a major compromise and it is very easy to find and pull off. Even a simple scriptkitty that is running a web server tester will find this exploit. /u/WilliamGibson I will be passing this information over to you. This shouldn't be a problem with even the most basic jailing practices on the web server layer.
Until such time as this is fixed nobody should use Versus. I can't say that enough. This entire server is probably compromised already by law enforcement and being monitored. It is a total compromise and is without a doubt one of the worse outcomes to a simple security exploit I have seen in a very long time.
-----BEGIN PGP SIGNATURE-----
iQIzBAEBCAAdFiEEbfleES3oPdbct1q5DE1JcU+sN9gFAmKETTgACgkQDE1JcU+s
N9jjpQ//avXy8kS1tMhVK4botRjGhXit+k88pwKwWnizwg+GQTaFCu+XCd3SrDa9
tjZrcgmaVYJYjr+lprKE/aSw9ak1go8D90631N59mTR6DRlBr4Q8c1O0uMKC8cX8
+ONi+JSN5QBiigtp1MC/mVIhQJeLdgx5bDl+MtJe0jXFK+t26WwvKpscbydr22kQ
0enYyhliHDp+ikH12gXVLGn2yLBMCi12UD3xxlCJDBB/nbzH10dY3L8qQmsyf0JV
dRV4YPpxKabui0yYxqrUy2uLGDxuyKx7thBG0zJyOg/Oewss2iRexGkxyomuw9be
82ijGWMHNKorNXwwgj41485cOknSsuPo3JaibQJr5BNESvjxCos2gbhnfJ10xXR+
SkM7hFQAJt28W1dV3/qXl+wV/iL1+VsxNBpjckDK+m+D4UsDwpS8eZkx1+Vq0jOI
qAQBubC/d9vLpQvgSqRUFdyiK+FTY/u6P3eXdTXJCB+AZ5wWfaUAiEKhstSK1Zba
W4Gh2TQSxgTZtmyh2NdahkRFTSe0NaGFx9FsDBA5gzL8PcVg8CqWuZwo4LH3/f8S
F2whSD9AUnPZ4mUpi4JzSVOOWyEL1cGiVni7Y5aKVdwWFEb6vWhEia178EOAjOjK
KlqkptcI1LMuy2DLPBK/c/vCW/NpbADUXj21X4DxRsxRwblyxHY=
=zt91
-----END PGP SIGNATURE-----
dread: dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad.onion/post/81fac8c141c9fc519b9f/#c-fa7cd8851e945ec830
“immediately compromised”
A user in the comments asked Paris why “you and your best friend desnake (the only market operator here that has actually has a market busted by LE) blow it wide open and you even make it an announcement?”
Paris responded:
You need to understand that the server with a simple exploit like this is immediately compromised. As in it has already been compromised for a long time. Unless law enforcement is sitting on their hands they have already pwned this entire server.
Priority for me is community safety. Which means immediate disclosure and warning. You may think that is fucking the community over but it’s not. The exploit is ALREADY there and probably has been there for a long time. Easily findable and a simple request crafted in a specific way exploits the file system access to basically whatever.
Limiting the damage caused is disclosing this and not having it behind closed doors to be fixed when the admins decide to fix it. They must move servers immediately and patch before bringing it up to the public. Right fucking now. Because right now it’s a free season and all the information to be had about versus’s server is up for grabs.
dread: dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad.onion/post/81fac8c141c9fc519b9f/#c-d447d6525bd3caefd6
Previous Incidents
I.P. Leak
In March 2020, Versus paused operations to conduct a security audit after a “a potential IP leak from one of our middleware server[s].” Versus staff posted an explanation:
What happened?
A few days ago a DDOS against Versus started.
The application layer of Versus is very strong, so it was tor failing sometimes.
The attacker found an application layer vulnerability by requesting non existing captcha images. This lead to a lot of useless file IO and exhausted the main server resources.
Changing the captcha system isn’t a quick fix, so we deployed a custom middle-ware on the tor fronted servers to deliver the captchas and filter bad traffic before it even gets to the main server.
To further improve the resistance of Versus we did a V3 load balancing test.
To not have to apply the middle-ware to all servers for this test, it was moved to a single server in the same DC the tor front-end servers.
The plan was to use one middle-ware server for every balanced mirror, not every tor instance.
A bad decision lead to an IP leak of the middle-ware server.
Versus was down for about 14 hours to move our complete infrastructure to other hosts. From every DC, not just the compromised one.
Some additional errors then popped up because bitcoin-core, monero-core and our database got updated to the most recent version.
How we fucked up.
A trace route showed a perfect loop-back on the middle-ware server IP so the request was routed there via IP as nothing would go beyond the first router.
THIS WAS A BAD DECISION MADE AFTER NEARLY 3 DAYS WITH NEXT TO NO SLEEP.
The middle-ware gets the onion and adds it to a custom header so that we see from which mirror the request is coming from, but instead of extracting the onion, it extracted the IP from the request (it’s own) and added it to the header.
The main server used this header to generate the 2FA message where the IP was shown.
What we did to avoid such stupid mistakes in the future.
The middle-ware was fixed to extract to correct onion under any circumstances.
The display of the hostname gets validated via regex.
There is no more routing via IP. The middle-ware will run on every single tor instance. The routing to the back-end server is also over Tor.
Additionally we checked the source to look for any other instance where the hostname/custom header might show up. Nothing was found.
This multiple layers of security will make sure, that even a bad decisions under sleep deprivation will not lead to such an event again.
Bitcoin Theft
In July 2020, Versus staff announced that someone had hacked the market and had stolen the majority of the Bitcoin held in escrow.
This is a post i hoped to never make but the foundation of Versus is honesty and transparency to our members. As of today, July 10th, we were hacked and a majority of bitcoin held in escrow was stolen.
We immediately took down the market and confirmed that no sensitive has been compromised. We are committed to identifying the vulnerability that was exploited and will not go back online until this is solved.
We know many of you are reading this and worried about your funds. We are going to do our best to make up for it just like we did with the lost XMR, either through refunds , reduced fees, free ads and more.
We also want to remind everyone that this is an unfortunate example of why MS is so important , your funds simply cannot be stolen.
Multisig payments are NOT affected and can be received with the presigned and timelocked raw transactions we provided vendors with.
To be perfectly clear: When we get back we will enforce multisig payments.
We know some of you may scream exit scam and we expect that. We aren’t going anywhere and will be back stronger and more secure than ever. We live, we learn.
The Versus Project is a lot more than just a market and we won’t abandon our vision.
To our community , thank you for sticking with us.
Going Forward
Markets rarely return after something like this becomes public. However, Versus has experienced this at least twice. The market is more popular now than in 2020 after both incidents described above.