Transcript of an IRS Presentation About the Darkweb and Cryptocurrency
The IRS, as some noticed on Dread, had a conference wherein they discussed the darkweb and various elements of cycbercrime as it relates to the financial sector. The presentation includes information about Alphabay, mentions DeepDotWeb, and has screenshots of Dread.
IRS Criminal Investigations Division Special Agent James Daniels gave a presentation on the fundamentals of cryptocurrency use in connection with darkweb marketplaces, fraud, and hacking. The presentation is a look at law enforcement’s perspectives and understanding of darkweb markets and cryptocurrency. The presentation is incredibly long. More than an hour. Much of the content is incredibly basic. The table of contents will prove useful. Sections have been removed for brevity.
The original source is the IRS.gov website. A pdf of the slides presented alongside the video (from which this transcript originated) are also available at the IRS website. Also note that the low image quality is the quality of the images as presented in the slide.
JAMES DANIELS: All right. So we’re going to jump into and start talking about the Deep and the Dark Web. This graphic here shows kind of a representation of what’s out there in terms of the Internet. And quickly, what this shows is that the Surface Web, which is the place that most people are used to and go majority of the time is at the very top. Down below with Deep Web, in order to gain access to that, these are private databases and password protected sites. Within the Deep Web, we’ve got the Dark Web, which is only accessible via special software; and is intentionally hidden and anonymous. So let’s dive into each one of these a little bit more. So, the Surface Web. This is accessible via normal browsers that you’re used to. Explorer, Firefox, Chrome. And they’re the normal websites you go to. Google, Yahoo, Facebook, those kind of places. It’s been part of the worldwide web since the first browser was introduced in 1990 and it’s a thing most people are familiar with. Anything you can discover through your Internet browser using any of the main search engines is what you get access to. This is where you read about the news, buy something on Amazon, or visit any of your daily sites. It’s also an area of the web that’s under constant surveillance by governments across the world.
The Very Basics
Everyone has access to the Surface Web. There’s nothing there that’s protected. The interesting note is this only makes up 5% of the total Internet content that exists today.
Estimates suggest the Deep Web could be anywhere from 500 to 5,000 times larger. In perspective, there are roughly 20 terabytes of data and roughly one billion documents on the Surface Web,compared to 7,500 terabytes of discovered data and almost 6 billion discovered documents in the Deep Web. So, let’s talk about the Deep Web. The Deep Web is part of the web at its conception. In its basic terms, it’s an opposite of the surface has it has anything that search engines cannot find. The key difference between the two in real data terms, sites on the surface in it are indexed for search engines to find, like Google. But the Deep Web is not indexed.
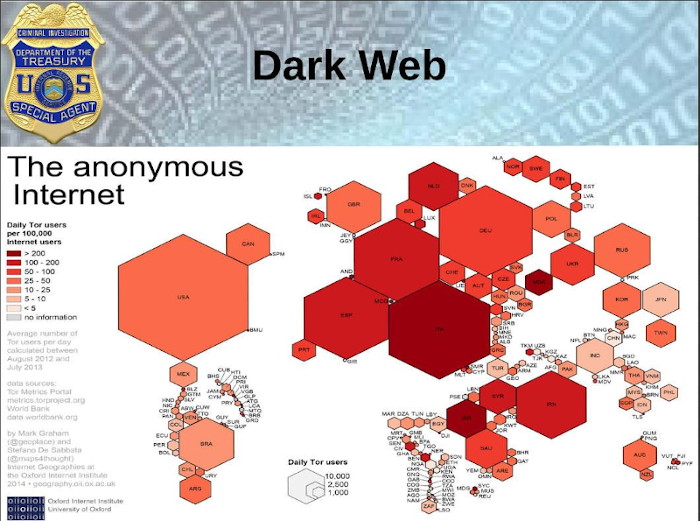
However, both are accessible by the public; they just require different methods to access them.
Usually, a specific password, encrypted browser, or a set of log-in details. The Deep Web contains the Dark Web, and it isn’t as bad as it sounds. But without it, we wouldn’t be able to It is this need to keep files that gave a rise to the need to keep a portion of the web secure and use the Internet as we do today. The Deep Web contains all of our medical records, financial records, social media files, and plenty of other information we want to and need to keep secure. away from the, quote unquote, Googled at the whim of anybody at any time. A good example is when you have to either generate a PIN number or have memorable information to enter across bank accounts often online. This information is stored in the Deep Web, and you have to use details like passwords and those kinds of things to allow you special access. But as you can see it, and you do still have access to the Deep Web, and it isn’t that entirely illicit dangerous part of the web that it’s often confused with. Which is what the Dark Web is. So the Dark Web is part of the Deep Web. But its major difference is that it has been intentionally hidden and is inaccessible to normal web browsers. The technology to create the Dark Web was initially created and is still funded by the U.S. military researchers since the mid 1990s. And the reason was, it was to allow spies and intelligence agencies to anonymously send and receive messages.
It’s named The Onion Router, and was quickly coined the shorter term Tor, T-O-R, with its name coming from the application layer encryption within a communication protocol stack. Basically, it represents layers of an onion in terms of encryption. If the military unit built it, why is it accessible to anyone with the right tools? Well, the strategy was to release the Tor into the public domain with simple logic. You can’t hide messages if there’s nothing to hide them behind. Therefore, if more people have access to send anonymous messages, it’s harder to find – for counterintelligence agencies to discover these messages.
Perceived Benefits to Tor Use
So the government opened it up to allow others to use it so they could use it to send messages back and forth, things that they didn’t want governments to know or other people to know.
Another perceived benefit was to help people in nations where they seemed to be oppressed.
With impossible freedom of speech laws to allow the voices freely where they cannot be tracked and punished. A good idea in theory. However, it has been primarily filled with crime and the ability to find these criminals is extremely difficult. Which is what the entire process and point of the Tor project was, was to make it impossible to find who’s communicating out there.
What is on the darkweb?
Now, one of the things I want to talk about is what kind of services or what is out there on the Dark Web? And one of the big things, just like most things on the Internet, is pornography. But, in this case with the Dark Web and it being anonymous, unfortunately, we see a lot of child pornography out there, and child exploitation. It’s done out here because of the anonymity of the Dark Web, because it’s difficult to find and track these people. The other thing we have is pharmaceuticals. People will end up selling extra medication that they’ve got out on the Dark Web, and doctors will end up selling medication that they get access to at a significant profit. People who aren’t allowed to buy weapons or want to buy weapons that aren’t necessarily allowed where they’re at, this is where they can get them.
There are blogs out there that talk about how to commit crimes. The blogs that go through and talk about ways to commit fraud, ways to commit identity theft, and even how to steal from the government, how to file false tax returns, and even commit other violations. There are financial fraud sites that specifically go through and show users how to go through and look for identifying information on people, and a system in exploiting the financial industry. There’s a significant amount of drugs that can be purchased out on the Dark Web. Fake documentation services where you can get passports created and/or driver’s license information created. There are carding sites where you can take credit card information and have them encoded onto new cards, or get access to other people’s account information.
[Snipped Q/A Portion]
How Does Tor Work?
JAMES DANIELS: All right. Sounds good. So the question is, how do people access the Dark Web? Well, actually, it’s not very difficult to do. It requires special software that needs to be run on your computer, and one of the ways you can do it is a software by the name of Tor, which is free software enabling anonymous communication. The name is derived from the acronym of the original software project called The Onion Router. Another component to use with this is a software program called Tails, which relies on the Tor anonymity network to protect your privacy online.
[snip]
Onion routing is implemented by encryption in the application layer of the communication protocol stack. Nested like layers of an onion, Tor encrypts the data, including the next node destination IP address. Multiple times it sends it through a virtual circuit comprising of successive random selection Tor relays. Each relay decrypts a layer of the encryption to reveal the next relay to go to. The final relay decrypts the most inner relay, and then sends the original data to its destination without revealing or knowing the source of the original IP address. Because the routing of the communication is partly concealed, at every hop in the Tor circuit, the method eliminates any single point at which the communication peers can be determined through network surveillance that relies upon knowing its source and destination. And these Tor nodes that are out there are just volunteer computers.
[snip]
So let’s look a little bit more into the Tor browser itself. When you open up the Tor browser. It is based upon Mozilla’s Firefox, and is preconfigured to protect your anonymity. It does this through plug-ins that it uses directly for Firefox. Now again it does not protect your computer from malware or viruses or anything like that. Once you open up the Tor, you can click on the link shown here, and then that will take you and open up and show you what your IP address appears to be. Now, on this slide, your IP address is shown in the middle. I’ve got it circled in red. If you were to open up a browser that was not using Tor, this IP address would be different. Again, this is important if you’re attempting to conceal where you’re at or where you’re trying to communicate from.
A good example would be, you know, you coming from a different address, house address, than the one that you actually live at. You can say one, but you’re actually at another. It just allows another relayed node in between. So then that way, whatever website you go to, this is where it will appear to be coming from, even though you aren’t actually coming from that location. Now, in the upper corner, there is a little onion, part of this Tor browser. If you click on that, that will actually take you to the notification of where your relays are going. And on here, you can see that the browser is connecting through three different hops. One goes through France, then through Germany, and then through the United States. So these are the connection Tor nodes that you’re actually hitting when you’re going through this particular Tor connection. Now, this one here, if I was attempting to make it look like I was coming from the United States would be the one that I would want. But if I did not want this particular communication link to make it look like I was coming from the U.S., I could click on the very top where it says new identity, and it would give me three brand-new Tor nodes that I would go through. And I can keep clicking that as many times as I want to get the actual connection that I want. You can also close down this software itself and reopen it, and that would give you a new connection as well. So depending upon the level of security that you’re looking for would depend upon how often you would redo this identity.
[Snipped Q/A Section]
PHILIP YAMALIS: So if I’m petrified of the Dark Web and I’ve got Chrome and Explorer on my computer, I don’t really have to worry about accessing the Dark Web because I’m not going to be able to put Tor on there, unless I use that special software.
JAMES DANIELS: Correct. If you don’t have the special software, you can’t get to the Dark Web. Kind of like if you’ve got Microsoft Word document. If you don’t have Word, you can’t open it. Now, you may have another piece of software, maybe Google has a piece of software that can open up a Word document or Office can open it up, but you have the right software in order to get to it.
PHILIP YAMALIS: Got it. Why don’t we continue and talk about searching the Dark Web.
JAMES DANIELS: All right. So, getting into the Dark Web and actually looking around, you have to go to something other than Google. And there are a couple of websites that are out there, and I say websites, these are dark websites, that you would go to. And one distinction, you know whether you’re on a dark website or a regular website would be the address of the website itself. The .onion at the very end distinguishes a dark website from a regular website. Normal websites have on a .com, .org, .info, etc. Dark net websites have a .onion address and agian that onion is for that layer of that encryption.
.onion Addresses
That’s what it’s referencing in terms of the onion layers. So in here, you’ve got the Onion URL Repository. And basically, it’s a massive index of over a billion page results and it doesn’t have limitation on the type of information it holds. Another one would be the Uncensored Hidden Wiki sites. Again, this is another website that has an uncensored collection of links and articles over the site’s history, and they’ve included links to information on criminal activities from drugs to child pornography. There are still links to graphic content and illegal sites can be found on there.
- The NotEvil website is a search engine that allows users to skip over any ads or any other information and specifically get to what they’re looking for and kind of acts like and mimics Google.
- ParaZite is another search engine that works on the Deep Web. It has basic useful features to allow people to get around. Now, one question usually comes up, why is the Deep Web search not available from Google? Well, the primary reason is Google doesn’t provide Deep Web content, in that this content is not indexed with regular search engines. Hence, search engines will not show the results, or crawl to a document or file, which is unindexed by the worldwide web. The content lies behind HTML forms, which is the basic storage mechanism of web pages. Regular search engines crawl and searchs are derived from the interconnected servers that they have access to. And again, only 4 to 5% of the internet content is actually visible to the general public. The other 96% is hidden behind the Deep Web. So, let’s take a look at one of these search type engines.
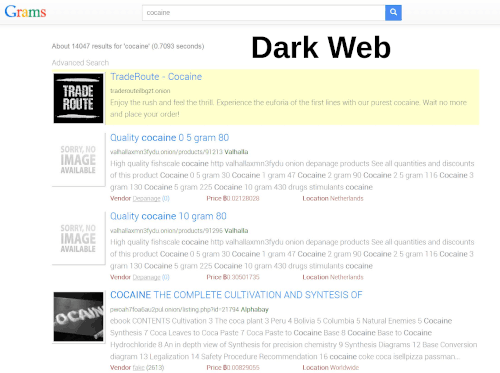
- One of the ones that used to be in existence out there and now no longer is is called Grams. A lot of these websites come up and down all the time. But in this particular example, I just went to the search browser and typed in cocaine. And when I hit the search engine, it came up with various number of Dark Net sites that allow me access to purchase cocaine in various amounts, sizes, and from different locations. So, depending upon where I wanted to get it shipped from or depending upon the volume or the amount I wanted, I’ve got the ability to use these type of search sites to go out to the Dark Web. So a lot of these sites aren’t openly accessible.
DeepDotWeb Mention
There isn’t just a place to go and look them up. So, some websites have popped up, and one of them here is called the DeepDotWeb. On here, they give you a list on the Surface Web of a lot of things that are happening out on the Dark Web. Where to go. Websites you can go to. Marketplaces you can go to, and blogs and forums that you can join. They also have a equivalent of a .onion address, which you can see and hear that they give their deep.dot.web onion address on there as well.
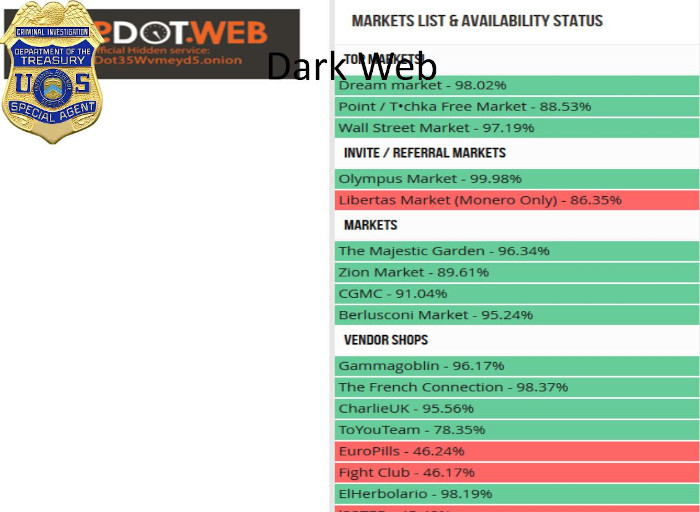
And if you can go and access it through the onion address, you can directly link to these websites while you’re in the Dark Web. It’s also a new site dedicated to events in and surrounding the Dark Web, featuring in-depth interviews and reviews about dark net markets, Tor hidden services, legal actions, privacy, bitcoin, and other really big news. So, let’s take a look at some of the Dark Net markets. I’m going to describe basically what a dark net market is. What it is, it’s the equivalent of Amazon, but in the Dark Web. So, if you wanted to use Amazon to go and buy a set of speakers for your computer, you would open up Amazon and type in what you were looking for.
Computer speakers. And you would get a series of customers who are willing to sell that product to you. You can browse and see the prices, the types, how much they’re willing to sell it, if there’s shipping costs. The Dark Web has the exact same thing. And your equivalent is called a Dark Net market. And these Dark Net markets do the exact same thing that Amazon does. But, their categories are a little bit different. As you can see on this page, you can browse for categories for fraud, drug and chemicals, guides and tutorials, counterfeit items, jewelry and gold, weapons, et cetera. So, categories are different than what you would see on Amazon, but the look and feel are the same. Even on this page here, you can see postings for particular featured items. Now out on the dark web, people don’t operate under their normal real name. That’s why they’ve got here. They’re here because they want to be anonymous.
Using Alphabay
So when they’re there, they have a user name or a user handle to go by, and they come up and make a fake name. In this particular example, we’ve got a user name of angrydragon007. And with that, this person now can operate underneath that name. And everyone out on the Dark Web knows them as that name, and that’s the name that you operate under, that’s the name you communicate with, that’s what you buy under, and that’s what you sell under. And the main reason is, people want to have confidence in who they’re dealing with. They may never have met this person in real life, but, in operating underneath this name now, now they can go out and see, hey, who is this person? This is the person I want to communicate with.
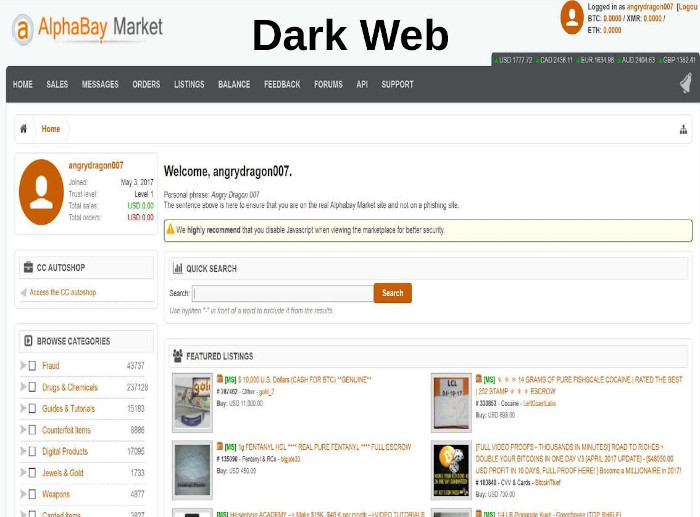
I don’t know who their real name is. I don’t know where they live. But I know and possibly can trust this person to interact with and do transactions with. And a lot of these websites that are out there allow you to basically rate the transactions as well. So, if I want to buy some heroin, and I click on this, I would look at what kind of rating that this person had, and they would either have four or five stars, just like you would see on Amazon. It’s no different. And the main reason why they want to do that is if somebody starts to get bad ratings because they’re now sending out what they had promised, then nobody’s going to transact with them. So, it is a self-sustaining market that works because of the anonymity and for this feedback. So this type of website basically allows for people to do anything that they want.
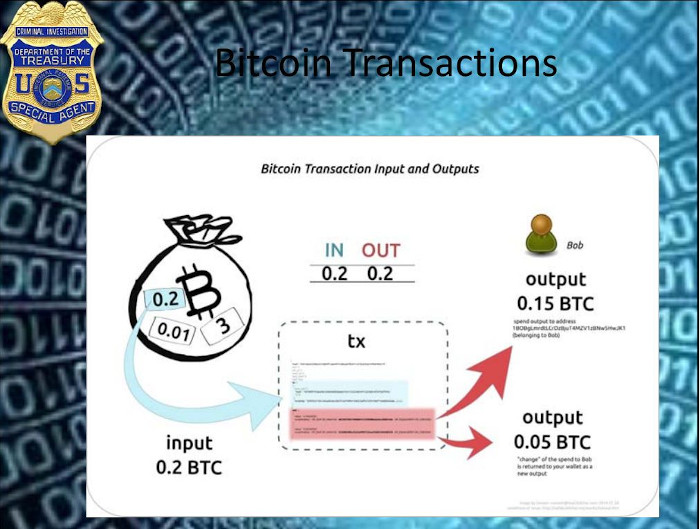
Now, this AlphaBay Market is no longer active. It was taken down by law enforcement. On July 20th of last year. It was a globally coordinated operation between law enforcement agencies worldwide. The United States Department of Justice announced the takedown of AlphaBay and Hansel Marketplace at the same time. It offered a bunch of different listings, including illegal drugs, firearms, and stolen personal identifying information. Payment was regulated using bitcoins. And that’s another significant thing with these types of Dark Net marketplaces, is they don’t take credit cards.
They take virtual currency. And they take different types of virtual currency depending upon what’s being sold. So, if it is a transaction for some PII, which is personally identifiable information for someone else, maybe that particular seller will only take bitcoins. And so you would then transact with this person using bitcoins rather than real money. Other vendors may only take Monero or Ethereum. And so depending upon the type of payment that they’ll take will depend upon how you conduct that transaction with them. No different than what you see out on Amazon or e-Bay or something else like that. E-Bay may say, hey, we’ll take Paypal, we’ll take credit card, but we won’t take checks. This operates the same way, but it’s with virtual currency. They also have escrow accounts as well to protect buyers and sellers. It would allow you to go in and basically make a payment, and the escrow company on the Dark Web would hold that until you agreed that, yes, I got this, and now I feel comfortable releasing the money. So there’s also that set in there as well that helps protect both sides, if you will. So I’m going to talk a little bit more about the AlphaBay Market takedown.

So AlphaBay was reportedly launched in September of 2014. At the time, it had about 14,000 new users in the first 90 days of operation. Dark Net informal website placed AlphaBay Market at the top tier of the markets in the first six months that it had been operating. In October of 2015, it was recognized as the largest Dark Net market according to Digital Citizens Alliance. In May of 2015, the site announced an integrated digital contracts in escrow system, which I had talked about. October of 2015, it had over 200,000 users. And by the time it was taken down in July of 2017, it had over 400,000 users. AlphaBay was known in the world of dark markets for accepting other currency types other than bitcoin. It had support for Manero and other types of crypto currency.
Some interesting articles that came out about AlphaBay Market were, in March of 2015, AlphaBay made the news for selling stolen Uber accounts. Uber had made a statement regarding the potential data breach. We investigated and found no evidence of a breach. Attempting to fraudulently access or sell accounts is illegal and we notified the authorities about this report. It’s a good opportunity to remind people to use strong unique user names and passwords and avoid re-using credentials across multiple sites and services. In 2015, London-based telecommunications company, TalkTalk, sustained a major attack. The stolen data was put on sale on AlphaBay, which led to the arrest of a 15-year-old boy who had done the hack. In December of 2015, a website called code breaker released a podcast describing shopping experience on the marketplace. The podcast talked about purchasing illegal items on the marketplace such as pharmaceutical drugs.
The UK based media outlet Daily Mail pointed to the marketplace that might be linked to the Russian Mafia. According to the UK-based media outlet “Daily Mirror,” it’s administered in Russia By July of 2017, AlphaBay was ten times the size of its predecessor Silk Road, which was and has a Russian computer server. Expert claims it has links to the country’s Mafia and has proven impossible to shut down. taken down in October of 2013. Silk Road was also taken down by the United States as well.
It had over 39,000 listings, 400,000 users, and was facilitating between 600 and 800,000 transactions per day. By the time the first service began, Diaz used his hot mail address, and this would be Alex, the main organizer of this particular Dark Net marketplace. And this is how we as the United States ended up figuring out who this was. He had used a pseudonym to run the sites, which he had previously used in other carding forums in 2008. This is where it comes into when I was describing before about when you pick a user name, everyone sticks to it on the Dark Net market sites, because if you move and change user names, you have to rebuild up your credibility.
Alexandre Cazes
Diaz’s [sic] laptop reportedly contained unencrypted personal net worth tapping to all of his global assets across jurisdictions at the time he was captured. He also had servers which contained multiple and consistently unencrypted crypto currency wallets. That’s where the majority of his profits went. Assets were liquidated through proceeds were held in a variety of accounts directly related to Diaz’s wife and companies they owned in Thailand, or directly held in personal accounts in Liechtenstein, Cypress, Switzerland, and Antigua. The statements about the goal on his site that he launched in 2014 and his goal was to become the largest e-Bay style under world marketplace. In May of 2017, law enforcement was active on the site. In June, a warrant was issued by the United States and the eastern district of California for racketeering, narcotics, identity theft and access to {indiscernible}. Transferring of false IDs, trafficking illegal device, and making equipment and conspiracy to commit money laundering.
A warrant was issued for his arrest in Thailand by the end of June. In early July of 2017, Canadian police raided a company in Montreal. It was his company and it was the reported location of the physical servers as well as two residential properties. He was arrested in Bangkok at his dwelling in a district which was searched by the royal Thai police police with the help of FBI and DEA. He unexpectedly committed suicide while he was in custody of the narcotics division in Bangkok. His wife has also been reported to be charged with money laundering, and by the end of July, the site was shut down. So that’s just one example of one of the investigations that we end up doing. There were many other sites that we have taken down, but AlphaBay was one of the main ones. Why don’t we go ahead and go to our next polling question.
[Snipped Q/A section]
JAMES DANIELS: We’ve got the, this is what the Dark Web is and this is what happens out there. And the connection to the CPA and the tax – because, again, I’m a criminal investigator with the Internal Revenue Service, and all of these things impact tax administration and the collection of the appropriate taxes that need to be paid. All of these industries are taxable when you talk about drugs and money laundering and all of these things. If there’s a profit being generated, it has to be taxed as well, in addition to it being money laundering. Now, from the CPA perspective, the biggest thing to take away is this is where the CPAs and small businesses, they get hit and they get hit hard. So, what we have seen and we’ve been working on is there are websites out there that are specifically dedicated to supplying access to CPA firms and tax preparation companies and their service.
Identity Theft
So what we’re seeing out there is the identity theft that’s occurring. Is that we are having the malicious software that’s out there is being downloaded inadvertently or intentionally onto computers’ machines. And when that happens, it gives access to that particular computer. And CPAs and tax preparers, they’re the ones that have the majority of the information. So I’m going to get in and talk in a little bit more depth later about that. But that’s going to be the connection to the CPA and the tax preparers that are out there, is knowing what is out there on the Dark Web, knowing what occurs out there, and that you’re subject to your information being out there as well because it either was stolen or captured at some point in time.
“The Opioid Crisis”
A lot of that is being done specific to help and support different drug habits like the opioid crisis that’s going on right now. So I’m going to quickly touch on that, what’s occurring out on the Dark Web right now. We as federal agents, both with the IRS and DEA, FBI, are working with HSI, which is Homeland Security Investigations, to help combat this opioid crisis. And we’re seeing that pop up more and more on the Dark Web itself.
With this, the root causes of the current crisis are complex. And one of the solutions federal agencies have developed and implemented to help stem the tide of opioids coming into communities is relatively simple and straightforward. Leveraging the unique authorities and broad resources of HSI to disrupt, dismantle, and defeat the transnational criminal organizations and disrupt networks responsible for the current crisis identifying and targeting upper echelon traffickers, seizing their assets, and holding them accountable for the destruction they are responsible for.
To accomplish this, HSI is determined to target these individuals along with other federal agencies, wherever they are located, including in the deep recesses of cyber space. As a result, those who traffic in opioids, particularly within the Dark Web, are a top priority of the federal agencies. Dangerous and often fatal substances such as Fentanyl and other synthetic opioids as well as heroin and illicitly obtained prescription opioids are increasingly being distributed online via the Dark Web, requiring new and innovative technologies that law enforcement must implement. So the other thing to remember with this whole opioid crisis and everything that’s going on, this all comes back to money, and allowing money that’s being transacted on the Dark Web, almost all of it is being done through virtual currency. And this is the other avenue that [indiscernible] comes into, is there is a very large subset of people that are using virtual currency to conduct illegal activities.
So, if you’re a CPA and you have a client that is involved in this type of activity in terms of operating with virtual currency, it may be worthwhile to inquire as to what are they using it for.
HSI Cyber Crimes Center
Because some of this virtual currency is being used in the Dark Web for illegal activity.
Let’s go ahead and go to the next slide. This is a package – a picture of a package of opioid type material and drugs that are being delivered through the postal system. And one of the ways that you can do this in terms of this information being – the drugs themselves being moved through our postal service is because of the Dark Web. The Dark Web through these Dark Net markets are allowing these dealers to set up and have complete distribution systems set up to go from where they’re being either made out of the country and/or from illegal prescriptions in doctor’s offices and other ways, because leveraging the Dark Web and the anonymity of it that it allows, allows for this type of activity to occur. Okay. Let’s go to the next slide.
So, at the forefront of this activity, is the HSI Cyber Crimes Center, which is also identified as C3. The personnel at C3 are devoted to spearheading and coordinating transnational investigators that originates from illicit trafficking of opioids within the Dark Web. Federal agents, intelligence analysts and other personnel assigned to C3 have spent years honing and refining their skills in penetrating and navigating the Dark Web and routinely collaborate with each other, the personnel domestically and overseas to develop investigative strategies that have been critical in piercing the anonymity of users and administrators in Dark Net marketplaces. Training has been increased along with intelligence, which is a critical pillar in a multi-pronged strategy to the newly enhanced online undercover capacity that has been highly successful in penetrating these online narcotics distribution networks. All right. Go to the next slide. The digital nature of all of these things also leads back into the financial component we were talking about. The data you see during these previous Dark Web investigations, in many cases aggregated by federal agents and other law enforcement agencies to be made available for them to work their investigation.
[Snipped Ransomware Section]
“Can We Take Down the Darkweb?”
JAMES DANIELS: Okay. All right. And so money laundering is the main key that runs into us from an investigation standpoint, that that’s how
PHILIP YAMALIS: But I think the most important thing as you stressed earlier on the virtual currency is that on the Dark Web, they’re only going to use virtual currency as opposed to normal currency.
JAMES DANIELS: That’s correct. The Dark Web will only accept virtual currency because they want to keep their anonymity to a high. They want to make sure that they’re not transacting in something that potentially could be traced. Where virtual currency is more difficult to trace than using a credit card or a bank transfer or something like that. So the dark marketplaces out on the Dark Web will not accept payment other than in virtual currency.
PHILIP YAMALIS: You shared earlier the success of authorities to shut down some of the sites that we heard about and we read about them in the papers. One, of course, being AlphaBay.
How come the authorities aren’t able to completely shut down the Dark Web? How are you successful in shutting down things like AlphaBay, but yet the authorities cannot shut down the Dark Web?
What’s the reason?
JAMES DANIELS: Well, the thing to remember is the Dark Web was actually created by the U.S. government.
PHILIP YAMALIS: How about that?
JAMES DANIELS: And they use it to communicate, you know, sensitive information back and forth.
They’ve created an environment to do that. And they need that environment in order to have that encrypted communication and they need others to use this same tool in order to hide their messages back and forth. So, taking out the Dark Web is not what the intended purpose is. It just happens to be being used for the wrong purpose. And people are finding a way to use it for illegal things. Just like anything else in the world, somebody’s going to find a way to turn something into a criminal enterprise, and that’s where federal law enforcement has to get involved and attempt to dismantle that as much as possible. Now, we’ve got our own investigation techniques that help us trace and track people doing these type of things, and when we find them, we will take them out. But in terms of the Dark Web, it’s out there for an intended purpose. It just happens to be others are exploiting that purpose for criminal means.
Is There an Alphabay Replacement?
PHILIP YAMALIS: James, are you aware of a replacement for AlphaBay on the Dark Web? Has a replacement, have other great replacements for AlphaBay been created that you’re aware of?
JAMES DANIELS: Yes. I mean, as soon as AlphaBay went down, I think Dream Market was the next one that came up. And when Dream Market goes down, there will be another one that pops up. Like I said, we took out Silk Road, which was one of the very first Dark Net marketplaces. Others have popped up and we’ve taken those out, and it’s just a matter of continually taking them out and attempting to dismantle, you know, these illegal marketplaces that are transacting in, you know, these types of goods and this illicit activity.
“How is the Dark Web getting Social Security numbers”
PHILIP YAMALIS: Very good. And I know we’ve talked about this. How is the Dark Web getting Social Security numbers, even those of children?
JAMES DANIELS: Through data breaches.
It comes through the malicious code that gets installed on servers and, you know, CPA machines and normal businesses, their account files. And then those account files are then downloaded to a person’s machine who will turn around and upload them to the Dark Web for sale.
PHILIP YAMALIS: That’s where the data breaches begin. That’s where our headaches begin here, right?
JAMES DANIELS: Exactly.
PHILIP YAMALIS: So… all right. This is something that ties in a little bit with what we spoke about this morning and today. So how do you pay for something that you find on the Dark Web? Of course, you wouldn’t use your credit card and your real name. How would you pay for the product?
JAMES DANIELS: That’s correct. That’s where virtual currency comes into play. What you would end up doing is converting your money, your cash, to a virtual currency. Then you would use your virtual currency to pay for things online. You can use that with a wallet. You can use that with your – you know, the public key.
[Snipped Q/A Section]
JAMES DANIELS: Yeah. Again, a majority of the data comes from data breaches, whether that be from a company or from a person’s, you know, personal drive or wherever. And then what happens is Those those identities go for sale out on the Dark Web, like on AlphaBay type markets, where you can buy identity information or lists of information, depending upon if you buy it in bulk, you can get it for 50 cents an ID. Now with that information, once you’ve got the Social Security number, you know, name, address, other identifying information, then that information could potentially be used to create false tax returns. Which then puts your clients into the precarious position that if tax returns have been filed and accepted by the IRS prior to your client filing, then that runs into some serious situations of you not being able to get your clients’ return through. And so it’s just that vicious cycle that occurs, once that name is out there, it can be sold multiple times and used multipletimes for many different financial crimes.
PHILIP YAMALIS: And the bottom line here is, we can’t keep ourselves absent minded thinking that it’s not going to happen to us. As tax practitioners, we’re more vulnerable because we have all this PII, Personally Identifying Information, in our computer bases, and the Dark Web basically goes after those types of computers. So it’s certainly more apt to happen to a tax practitioner than someone else out there. You made some great examples of the Uber case, of some other cases that occurred, where even these big companies didn’t think it was happening to them but it was. So as tax practitioners, I guess we have to be a bit more vigilant, right?
JAMES DANIELS: Oh, very much so. In terms of information needed in order to secure, you know, the finances and financial information that’s necessary, tax practitioners are the ones that have the most. And again, it’s not just tax crimes that occur.
Should Tax Practitioners Use Tor
Alright, so, as tax practitioners, should we be using a Tor setup when working with people’s taxes?
Should we be using this as a layer of privacy for our home Internet use? Does it work like a VPN?
JAMES DANIELS: So, again, it’s one of those things in terms of security level of what you feel most comfortable with. What information do you have stored on the machine that you’re using.
I definitely, if I was a tax practitioner, would take a higher level of security on the computer I’m using to prepare tax returns versus the one I used to surf the Internet and not store sensitive information on. So I think you need to apply the security level to the data that’s being stored. And I’ll be honest, I’ve talked to some tax practitioners that have a desktop computer that they use strictly for doing their tax returns that’s not connected to the Internet.
You can’t get to it other than being in the office. So depending upon the level of security that you want to take this to, will kind of depend upon how fearful you are of having something happen. And it’s one of those things that you’ve got to do the best you can and have the best processes, you can, but all of these things will add different levels of protection. Using Tor in conjunction with tax returns probably isn’t the saving grace of everything. Tor is just more for the communication protection. It’s not going to stop ransomware or malware from getting onto your machine. That’s more of the making sure that you’re not opening up those emails, you’re not downloading things that you don’t know about.
[Snipped Social Engineering Section]
Are Cryptocurrencies on the Darkweb Illegal?
One of the questions is, you spoke about today that people pay for things on the Dark Web using the crypto currencies.Is this legal? Aren’t crypto currencies used on the Dark Web being done so illegally?
JAMES DANIELS: Right.
For this question, I like to use the example that people buy and sell drugs using cash. The mere fact that I have cash and I’m buying drugs, yes, that’s an illegal transaction. Now, if I have cash and I go out and buy a cup of coffee, not an illegal activity. It’s not an illegal transaction. Virtual currency is the same way. I can use virtual currency to buy something illegal on the Dark Web. I can buy cocaine with it. Now I’ve conducted an illegal transaction.

Or I can use virtual currency to go down and buy a Tesla. Not an illegal transaction. So you’re using the medium of exchange, whether it be cash, whether it be in virtual currency, but the mere fact that you’re doing the transaction in that is not the illegal part. The illegal part is what are you using it to buy. What are you using it to transact? What’s the purpose? That’s the part that’s illegal.
Cryptocurrency Conversion
PHILIP YAMALIS: Awesome. I love that analogy, and you used it earlier this morning, and it seems to enliven the discussion about the currency, the crypto currency.
Let me throw this one in about crypto currency. How do you convert virtual currency to Fiat currency, the currency used by the government? Will my bank automatically do that?
JAMES DANIELS: So banks, there are very few banks – I can’t think of any off the top of my head that will actually transact in virtual currency. Usually, what you have to use is a virtual currency exchanger. And so there are a couple of them out there. Some we highlighted this morning are CoinBase and Etoro. There is quite a few of them out there. But basically, you set up an account with them. And when you have an account set up with them, then they would allow you to convert from virtual currency to a Fiat currency like U.S. dollar or Euro or something else. So you have to go through an exchanger that will basically do that conversion for you. Or you’ve got to find someone who’s willing to, you know, buy your bitcoins or other virtual currency in some other way. So someone else has got to kind of make that conversion for you. Banks out there, up until now, have not been involved in doing any of that.
PHILIP YAMALIS: Very good. I’m going back to the Dark Web, because this person has asked that a couple times, so I’m going to go ahead and do it. It’s a two-(?).
Surface Web vs Deepweb
So, number one, this person asks, are user net sites part of the deeper web? And second, as someone who has no intention to purchase heroin to arrange for a murder or anything else nefarious,do I have any reason to ever go into the Dark Web?
JAMES DANIELS: Ok, so to answer the first question, yes, a user site where I needed a user name and password to get into, that would be, yes, part of the Deep Web, because that’s a protected area that no one can get access to, and that’s the way I kind of like to think about it, is with the Surface Web. Is it anyone can click on the site and look at the information without having to log in, then that’s the Surface Web. If I have to log in to either get my bank information, health information, or even into some social media part of like Facebook, some of it is public that everyone gets to see, some of it is private that only I get to see or who I decide to share it with gets to see. So that’s the distinction between the Deep Web and the Surface Web. So, the difference between the Dark Web and the Deep Web is – yeah, there’s probably no reason for that person to ever want to or need to go to the Dark Web. Again, it’s normally – it’s used from the illegal perspective of what we talked about, the criminal activities for drugs, you know, pornography, carding, all of those kind of things. And it is also used for legitimate purpose for securing communication back and forth. If you needed to communicate with somebody that you didn’t want anybody else to know about, that’s how you would do it. That’s how the government uses it. There is a legal avenue for using the Dark Web. But in terms of your normal everyday person, the answer is no.
Legal Examples of Darkweb Use
PHILIP YAMALIS: Okay. And once again, give me a legal example of using the Dark Web.
JAMES DANIELS: Perfect example would be the government needs to communicate to another government for military action. Or you could be in a potentially politically oppressedcountry where you want to speak out and start a group to talk about a certain topic that maybe that particular government doesn’t allow you to talk about. And so this would give you a forum to do it. Those are the main uses for it, is for communicating anonymously back and forth.
[Snipped end of presentation notes]