Brave Browser Leaked DNS Queries for Onion Services
Brave, a browser that allows users to access onion services, had a bug that sent queries for onion addresses to public DNS resolvers.
Brave is a browser that advertises itself as a privacy-oriented browser with built-in support for blocking advertisements, disabling javascript, blocking cookies, and similar tasks. One of the more recent additions to the browser is a feature called “Private Window with Tor.”
In this case, the browser’s adblocking capabilities–which, in and of themselves, are not anymore useful than an adblocker or PiHole–are at the core of the DNS leaks. TheHackerNews.com aptly described the DNS leak issue within the scope of the browser’s ad-blocking features:
This issue stems from the browser’s CNAME ad-blocking feature that blocks third-party tracking scripts that use CNAME DNS records to impersonate the first-party script when it is not and avoid detection by content blockers. In doing so, a website can cloak third-party scripts using sub-domains of the main domain, which are then redirected automatically to a tracking domain.
This feature of the browser is–or was–immediately noticeable by anyone using a local DNS sinkhole or checking DNS query logs. And for those running their server and the unpatched version of Brave browser, testing the bug is easy.
Brave allows users to open onion services in a Tor-enabled tab,.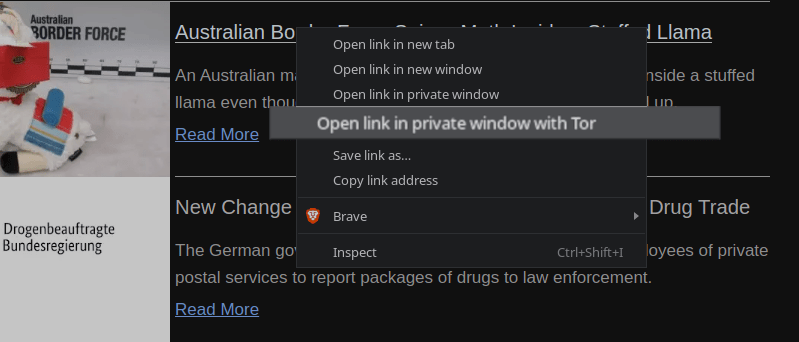
Tail your DNS query logs (or temporarily enable logging) and then, using Brave browser, right-click a link and “Open link in Private Window with Tor.” Your DNS server should pick up a query for an onion service.
Testing a DNS blackhole vs Brave's onion service implementation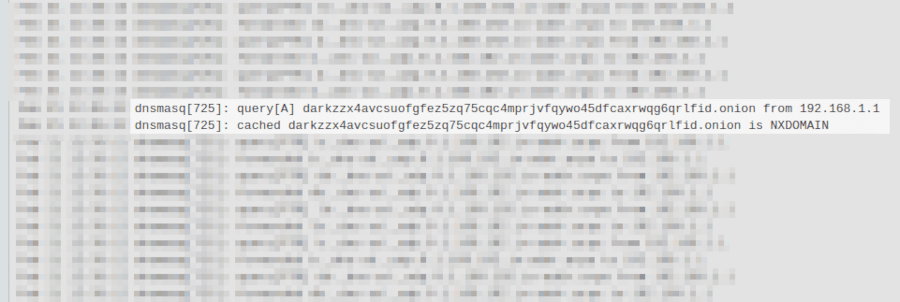
A report on the bug bounty platform HackerOne highlighted this issue on January 13, 2020. A nightly release of the browser reportedly included a patch for the bug. Brave had scheduled an update to the browser that included a patch for the DNS leak in Brave 1.21.x but only released an update to the public version of Brave after the public disclosure of the bug.
Of course, nobody should be using Brave browser to access onion services. A certain organization ships its browser that interfaces with onion services. The Tor Browser is a clunky FireFox-based browser that, by default, limits the browser’s ability to thwart your attempts to browse onion services privately. The Tor Browser has had flaws in the past that deanonymize users but, for the most part, these issues only impacted users that allowed javascript and made no additional effort to remain anonymous.
On the topic of using Tor Browser instead of Brave for onion services
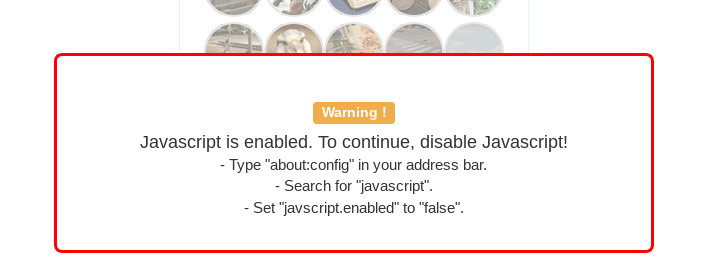
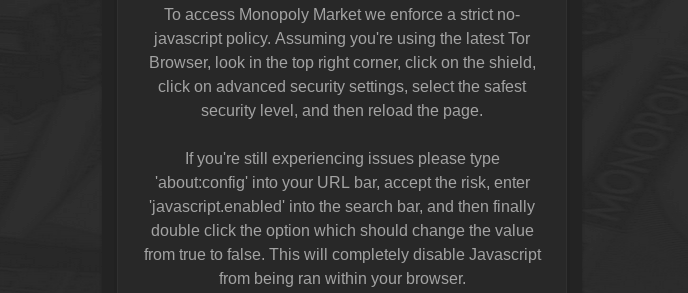
Security-focused markets such as Monopoly, White House Market, and others turn javascript into a non-issue by forcing users to disable javascript.
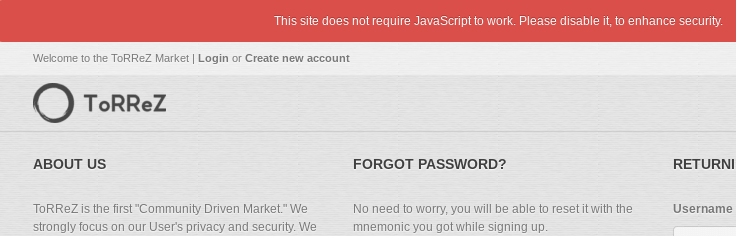
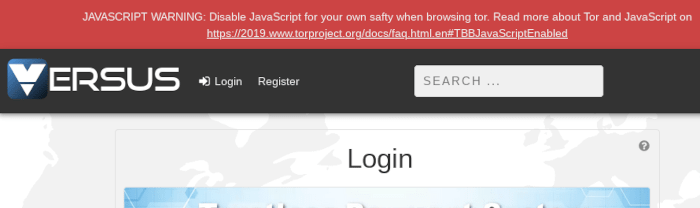
Others, such as Versus (which is also a security-driven market) and TorRReZ, warn users with javascript by attempting to load a couple of lines of javascript; if the javascript is blocked by the browser, the user experiences no change.
If it is not blocked, a style is applied to a warning banner that appears at the top of the window.
Read More:
- Cimpanu, Catalin. “Brave Browser Leaks Onion Addresses in DNS Traffic.” ZDNet, ZDNet, 19 Feb. 2021, http://web.archive.org/web/20210219160237/https://www.zdnet.com/article/brave-browser-leaks-onion-addresses-in-dns-traffic/.
- “Privacy Bug in Brave Browser Exposes Dark-Web Browsing History of Its Users.” The Hacker News, 20 Feb. 2021, https://web.archive.org/web/20210221001056/https://thehackernews.com/2021/02/privacy-bug-in-brave-browser-exposes.html.
- “Brave Browser Leaks Your Tor / Onion Service Requests through DNS.” [RAMBLE], 18 Feb. 2021, http://web.archive.org/web/20210219111003/https://ramble.pw/f/privacy/2387.
- Brave. “[Hackerone] Tor DNS Issue · Issue #13527 · Brave/Brave-Browser.” GitHub, http://web.archive.org/web/20210219125021/https://github.com/brave/brave-browser/issues/13527.