Brave.com Is Now Available as an Onion Service
Brave, the Chromium-based browser that sells itself on privacy and adblocking features, launched a version of its website for Tor users.
In a recent blog post, a Devops Engineer at Brave announced the creation of a Brave.com onion service (brave5t5rjjg3s6k.onion). Brave is fairly straightforward about the purpose of the onion service. Unlike many high-profile companies with onion services, Brave’s recent creation appears to exist for more than just optics.
“…we wanted to make our website and browser download accessible to Tor users by creating Tor onion services for Brave websites.”
An onion redirect using the Onion-Location HTTP header | Source: Brave
“These services are a way to protect users’ metadata, such as their real location, and enhance the security of our already-encrypted traffic. This was desired for a few reasons, foremost of which was to be able to reach users who could be in a situation where learning about and retrieving Brave browser is problematic.”
For a company that specializes in blocking and serving advertisements, Brave included unusually helpful information in their blog post. Specifically about using Alec Muffett’s Enterprise Onion Toolkit (EOTK) and obtaining their current EV certificate. The overwhelming majority of onion services have no use for SSL certificates. As a result, we rarely see the process of obtaining such a certificate documented (in this context).
“One snag was that the process of proving you own the address requires a few different steps of validation. One is the traditional EV due diligence of contacting a representative of the organization that is on-file with DigiCert. Another is a practical demonstration, either of a DNS TXT record or a HTTP request to a well-known URL path. Since the onion addresses don’t have the concept of DNS, TXT validation will be impossible. That leaves the only remaining option as the HTTP practical demonstration. The demonstration involves requesting a challenge from DigiCert, at which point they will send you a short string and a path that they need to see the string served at.”
At one time, DigiCert was the only provider of SSL certificates for .onion addresses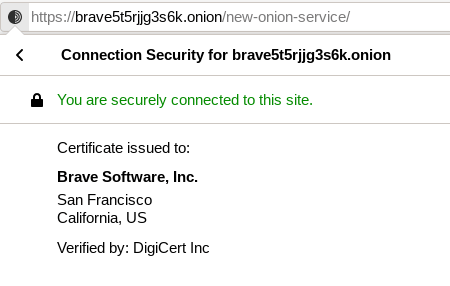
“You then start a web server listening on that address on port 80 (non-SSL). They will send a GET request for that path. If they are able to successfully fetch the string, they know that you are in control of the address. Sadly, when I performed this song and dance with DigiCert the request did not work for 2 reasons. One was that EOTK was redirecting all of the non-SSL traffic to the SSL listener. The request failed since we were still running an EOTK-generated self-signed certificate.”
DigiCert’s automated validator for SSL certificates is unable to route Tor traffic, according to Brave. It appears as if Brave had to open a chat session with a DigiCert employee to finally get things working.
Brave.com is available over Tor at the following address: brave5t5rjjg3s6k.onion.
On a related note, Security Boulevard has an interesting article on identifying the public I.P. address of an onion service using its SSL certificate. That is available here.