CipherTrace Uses Honeypots
CipherTrace, a blockchain intelligence company owned by Mastercard, uses “honeypots” to gather information about Bitcoin addresses, according promotional material sent to a government official.
A Freedom of Information Act (FOIA) request from CoinDesk asked the Treasury for emails that “included the word ‘cryptocurrency’ or several synonyms (‘virtual currency,’ ‘digital asset,’ etc.) or mentioned prominent companies in the industry like Coinbase or Ripple.” In the trove of documents received nine months later, CoinDesk found an email sent to then-Treasury Secretary Steven Mnuchin by the CEO and co-founder of CipherTrace.
FOIAd CipherTrace Slides
The slide contained a graphic not found on their public-facing material.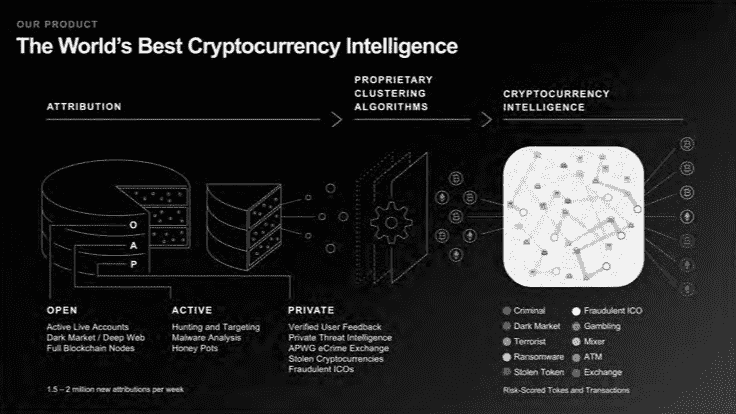
The email contained promotional material in the form of slides about the services provided by CipherTrace. Like Chainalysis, CipherTrace advertises “blockchain intelligence” services to the public and private sectors. The slide shared by CoinDesk appears to be part of a set of promotional materials for CipherTrace’s “CipherTrace Inspector” suite, which the company describes as:
“A suite of powerful and easy-to-use de-anonymization tools for law enforcement. Investigators use this integrated platform to obtain solid evidence on individuals who use Bitcoin to launder money, finance terrorism, or carry out drug dealing, extortion, and other crimes. The intuitive CipherTrace visual environment allows even non-technical agents and analysts to easily identify and trace criminals who attempt to use Bitcoin on the internet to conceal their illicit activities. The platform also supports de-anonymization for more than 800 cryptocurrencies — including Bitcoin Cash, Ethereum, and Litecoin. This de-anonymization capability spans more than 87% of global virtual assets.”
A picture of a promotional image from CipherTrace.
Unlike the publicly available datasheet and product page for Inspector on the company’s website, the slide sent to Mnuchin listed “honeypots” as one of the sources of data used by the company.
CipherTrace does not make this information publicly known. As a result, we do not know anything about CipherTrace’s honeypots.
Chainalysis as a honeypot example
However, unrelated slides from a Chainalysis presentation to Italian police revealed the way Chainalysis used a honeypot for years under the radar. CipherTrace’s tactics could resemble those employed by the industry leader, Chainalysis.
Somebody leaked Chainalysis material intended for Italian police.
The slides, which surfaced on Dark Leaks, the “decentralized information black market,” revealed that Chainalysis collected the I.P. addresses of people who used a block explorer secretly controlled by the company. When a user visits the site and looks at a specific transaction or address, Chainalysis associates their I.P. address with the transaction or address.
“Confidential” Slides from Chainalysis
In machine-translated English, the relevant part of the slide reads:
• Capability: Suspects may use walletexplorer[.]com to monitor transactions rather than checking exchanges directly for fear of leaving a “footprint”: The Exchange “scrapes” the suspects’ I.P. address. Chainalysis owns walletexplorer[.]com, and as such, we collect this data_._
• Results (empirical): Using this dataset, we provided law enforcement with meaningful leads related to I.P. data associated with a relevant cryptocurrency address. It is also possible to conduct a reverse lookup on any known I.P. address to identify other BTC addresses. It can also collect the data of an address of a data form that has yet to transit on the Blockchain - that is, ‘The BTC address provided as part of an investigation into a kidnapping or a threat to life - if the suspect checks his own address.
(I added emphasis where I suspect the automated translation may have failed. I am not entirely sure what the sentence in italics means. The URLs were also broken by me and appeared without the brackets in the slide.)
Wallet Explorer
The website’s only mention of Chainalysis was a footnote that stated, “the author of WalletExplorer[.]com now works [at Chainalysis] as analyst and programmer.” CoinDesk wrote an article about the slide, prompting Chainalysis to add a privacy policy to the site wherein they identified themselves as its owner.
The new privacy policy on WalletExplorer
WalletExplorer.com Privacy Notice
Last Updated: October 14, 2021
WalletExplorer.com, a Chainalysis website, is a Bitcoin Blockchain explorer designed to provide easy access to Public Blockchain Data (our “Services”) for our website visitors (our “Visitors”). This Privacy Notice explains how we collect, use, disclose, and otherwise process Blockchain Information and Visitor Information in connection with our Services. This Privacy Notice is not a contract and does not create any legal rights or obligations.
Our Collection of Blockchain Information and Visitor Information
Blockchain Information
When we use the term “Blockchain Information” in this Privacy Notice, we mean:
Public Blockchain Data: Blockchain is a shared, immutable ledger used to record transactions of assets, like Bitcoin. The Bitcoin Blockchain is a public ledger, meaning anyone in the world can view the transactions recorded on the Bitcoin Blockchain. Our Services are designed to pull the latest publicly-recorded transactions from the Bitcoin Blockchain every 1-2 days to provide our visitors an easy platform to review the following Public Blockchain Data:
Bitcoin Wallet Address: The unique Bitcoin Wallet address from which or to which Bitcoin is transferred.
Bitcoin Wallet Balance: The balance associated with the Bitcoin Wallet address.
Bitcoin Transaction Details: The transaction identifier, Bitcoin Blockchain position for the transaction, date and time of the transaction, amount sent or received, fee amount, Bitcoin Wallet Address of the sender and recipient, and storage size of the transaction.
WalletExplorer Blockchain Data: To make it easier for our Visitors to navigate the Bitcoin Blockchain, we supplement the Public Blockchain Data with the following data elements:
Wallet ID: Bitcoin Wallets may have one address or many addresses. To help our Visitors view Public Blockchain Data for a Bitcoin Wallet with multiple addresses, we use a mathematical function (known as “hashing”) to convert each Bitcoin Wallet address into a unique 16-digit alphanumeric identifier (the “Wallet ID”). Where multiple Bitcoin Wallet addresses contribute to the spending of Bitcoin in a transaction or “co-spend” on a transaction, we assume the addresses must belong to the same owner and link later Wallet IDs to the earliest Wallet ID assigned to an address within the Bitcoin Wallet giving each Bitcoin Wallet a single Wallet ID.
Wallet Name: A Bitcoin Wallet is a program for holding and transacting with Bitcoin. There are many companies that offer Bitcoin Wallets to the public so they can easily transact on the Bitcoin Blockchain. These companies collect a fee from users of their services and collect the fees in a company-owned Bitcoin Wallet. We are sometimes able to identify which Bitcoin Wallet Addresses belong to Bitcoin Wallet companies and, where we are able to do so, we assign a name to that group of addresses that replaces the alphanumeric Wallet ID (the “Wallet Name”). This Wallet Name is shown in lieu of a Wallet ID when available.
Visitor Information
When we use the term “Visitor Information” in this Privacy Notice, we mean the standard technical information we receive from Visitors to our Services when their browsers make a request to our website’s servers. Our servers automatically log Visitor Information, including the Internet Protocol (IP) address making the request, the website URL requested (which may contain the Wallet Name, Wallet ID, or Bitcoin Wallet Address associated with the page requested), the Visitor’s browser type and version, and other technical details used to ensure the website is delivered in the correct format (such as language and operating system type).
Our Use of Blockchain Information and Visitor Information
To Provide Visitors Our Services
We use Blockchain Information to provide our Services by permitting Visitors to review Blockchain Information either on our website, WalletExplorer.com, or via a dedicated Application Programming Interface (API) which allows our more technical Visitors to review the same Blockchain Information through their own computer processing programs.
We use Visitor Information to provide our Services by using the Visitor Information to deliver the requested URL to each Visitor.
To Otherwise Operate Our Services
We use Blockchain Information and Visitor Information to optimize Visitor experience with our Services, diagnose errors and problems with existing Services, develop and test new Services, and conduct research and analytics on Service usage and trends.
To Exercise or Comply with Legal Obligations or Rights
We use Blockchain Information and Visitor Information to exercise or comply with legal obligations and rights, including in connection with lawful criminal investigation requests.
Our Disclosure of Blockchain Information and Visitor Information
Our Other Business Lines
We share Blockchain Information and Visitor Information with our other Chainalysis business lines to help us deliver and improve those services. For example, other Chainalysis business lines may be able to use the information we provide to better connect one Bitcoin Wallet Address to another Bitcoin Wallet Address.
Our Service Providers
We engage third parties, such as website hosting providers, to perform certain functions on our behalf in connection with the uses of Blockchain Information and Visitor Information described above. Depending on the function the third party serves, the service provider may process Blockchain Information or Visitor Information on our behalf or have access to Blockchain Information or Visitor Information while performing functions on our behalf.
Business Transaction or Reorganization
We may take part in or be involved with a corporate business transaction, such as a merger, acquisition, joint venture, or financing or sale of company assets. We may disclose Blockchain Information and Visitor Information to a third party during negotiation of, in connection with or as an asset in such a corporate business transaction. Blockchain Information and Visitor Information may also be disclosed in the event of insolvency, bankruptcy, or receivership.
Legal Obligations and Rights
We may disclose Blockchain Information and Visitor Information to third parties, such as legal advisors and law enforcement:
in connection with the establishment, exercise, or defense of legal claims;
to comply with laws or to respond to lawful requests and legal process;
to protect the rights and property of us, our agents, Visitors, and others, including to enforce our agreements, policies, and terms of use;
to detect, suppress, or prevent fraud;
to reduce credit risk and collect debts owed to us;
to protect the health and safety of us, our Visitors, or any person; or
as otherwise required by applicable law.
Consent
We may disclose personal information about you to certain other third parties with your consent.
Personal Data
Certain information we process in connection with our Services may qualify as “personal data” or “personal information” under the laws of specific jurisdictions. Please visit our Chainalysis Privacy Policy for information relating to our processing of “personal data” and “personal information” and any rights you may have in relation to such data.
Children’s Information
Our Services are not directed to, and we do not intend to, or knowingly, collect or solicit information from children under the age of 13. If you are under the age of 13, please do not use our Services or otherwise provide us with any information either directly or by other means. If a child under the age of 13 has provided information to us, we encourage the child’s parent or guardian to contact us to request that we remove the personal information from our systems. If we learn that any information we collect has been provided by a child under the age of 13, we will promptly delete that information.
Third-Party Websites
Our Services may include links to third-party websites, plug-ins and applications. Except where we post, link to or expressly adopt or refer to this Privacy Notice, this Privacy Notice does not apply to, and we are not responsible for, any data practices of third-party websites and online services or the practices of other third parties. To learn about the data practices of third parties, please visit their respective privacy notices.
Updates to This Privacy Notice
We will update this Privacy Notice from time to time. When we make changes to this Privacy Notice, we will change the “Last Updated” date at the beginning of this Privacy Notice. If we make material changes to this Privacy Notice, we will notify you by prominent posting on the Services, or through other appropriate communication channels. All changes shall be effective from the date of publication unless otherwise provided.
CoinDesk emailed the company to ask about their use of honeypots. In response, CipherTrace sent, “A ‘crypto money pot’ or ‘honeypot’ is a security term referring to a mechanism that creates a virtual trap to lure would-be-attackers.”
I do not know what kind of honeypot(s) CipherTrace is using. Another block explorer website? Could they succesfully run a Bitcoin mixer? I expect any honeypot would need to provide as much data or the same type of data as Chainalysis’ WalletExplorer.
CipherTrace has appeared on Darknetlive in the past, as many will remember.
They provided the feds with a set of “Monero tracing” tools (“tracing” seems like a stretch but they used those words). They have two patents for tracing Monero. And they highlighted the movement of 69,370 Bitcoins in 2020 that someone had originally stolen from the Silk Road many years ago. A few days later, the feds announced they had tracked down the hacker, identified in court documents only as “Individual X,” and somehow “convinced” the individual to forfeit the Bitcoin to the U.S. government.
Also, CipherTrace is owned by Mastercard now and does business with the largest defense contractor in Europe, BAE Systems. It seems like they were a small-ish startup not long ago. Amazing.
They do have a neat Maltego transform though
The OP honeypot would be creating a cryptocurrency, encouraging criminal use of your coin, and then charging the federal governnment hundreds of thousands of dollars to trace these transactions. Or do the same thing as the feds…