A Collection of Articles About Hardening Linux
I tried to include primarily articles and readable guides, such as those published by madaidan. Also, I mostly tried to include some lesser-known articles. There are tons of security guides online and I do not want to simply recycle one of those. Some of the content, such as the articles about VPNs, are perhaps not going to be of interest to most of the readers of this site. Most of the older content is still relevent.
Android
A brief and informal analysis of F-Droid security - Wonderfall.dev
F-Droid is a popular alternative app repository for Android, especially known for its main repository dedicated to free and open-source software. F-Droid is often recommended among security and privacy enthusiasts, but how does it stack up against Play Store in practice? This write-up will attempt to emphasize major security issues with F-Droid that you should consider.
“Storage Scopes”, the new feature of GrapheneOS - wonderfall.space
A dive into how app storage works on Android. We will discover solutions implemented by AOSP and GrapheneOS to prevent invasive access to all of your files.
Android Tips - PrivSec.dev
Android is a very secure and robust operating system out of the box. This post will be less of a “hardening guide”, but more of a non-exhaustive list of tips when it comes to buying and using Android phones.
Android - madaidans-insecurities.github.io
this article explains common ways in which people worsen the security model rather than criticisms of the security model itself.
Desktop
Desktop Linux Hardening - PrivSec.dev
The goal is to produce a guide that intermediate to advanced Linux users can reasonably follow to set up and maintain the security configurations. It will also not try to be distribution agnostic, and there will be many distribution specific recommendations.
Linux - madaidans-insecurities.github.io
Linux being secure is a common misconception in the security and privacy realm. Linux is thought to be secure primarily because of its source model, popular usage in servers, small userbase and confusion about its security features. This article is intended to debunk these misunderstandings by demonstrating the lack of various, important security mechanisms found in other desktop operating systems and identifying critical security problems within Linux’s security model, across both user space and the kernel. Overall, other operating systems have a much stronger focus on security and have made many innovations in defensive security technologies, whereas Linux has fallen far behind.
Linux Hardening Guide - madaidans-insecurities.github.io
Linux is not a secure operating system. However, there are steps you can take to improve it. This guide aims to explain how to harden Linux as much as possible for security and privacy. This guide attempts to be distribution-agnostic and is not tied to any specific one.
Choosing Your Desktop Linux Distribution - PrivSec.dev
Not all Linux distributions are created equal. When choosing a Linux distribution, there are several things you need to keep in mind.
security-misc - kicksecure.com
security-misc: Enhance Miscellaneous Security Settings
The Linux Security Circus: On GUI isolation - blog.invisiblethings.org
There certainly is one thing that most Linux users don’t realize about their Linux systems… this is the lack of GUI-level isolation, and how it essentially nullifies all the desktop security.
Re: X11 -> Root? (Qubes square rooted) - seclists.org/dailydave
Fingerprinting
Articles
NetworkManager Minor Hardening | wanderingcomputerer.gitlab.io
MAC address randomization, Removing static hostname to prevent hostname broadcast, disabling sending hostname to DHCP server
How CSS Alone Can Help Track You - matt.traudt.xyz
A common question people ask when they first start using the Tor Browser Bundle is “why does the browser recommend I don’t change my window size?” Reasonable question. And if you disable JavaScript, you may think that’s enough to make window size irrelevant. Not quite.
Browser Tracking - madaidans-insecurities.github.io
Many common methods of preventing browser tracking are ineffective. This article goes over misguided ways in which people attempt to improve their privacy when browsing the web.
Don’t update NTP – stop using it - blog.hboeck.de
Today several severe vulnerabilities in the NTP software were published. On Linux and other Unix systems running the NTP daemon is widespread, so this will likely cause some havoc. I wanted to take this opportunity to argue that I think that NTP has to die.
Yardbird’s Effective Usenet Tradecraft - grugq.github.io
A few years ago a group of child pornographers was infiltrated by police who were able to monitor, interact, and aggressively investigate the members. Despite engaging in a 15 month undercover operation, only one in three of the pedophiles were successfully apprehended. The majority, including the now infamous leader Yardbird, escaped capture. The dismal success rate of the law enforcement officials was due entirely to the strict security rules followed by the group.
Post Hoc Ergo Propter Hoc Poop: Recorded Future and the Jihadi FUD-O-Sphere - krypt3ia.wordpress.com
Recently Recorded Future caused a stir in the media over what they gathered through OSINT on Jihadi crypto since the Snowden revelations. This report nearly made me have an aneurysm from it’s simplistic approach to the problem and it’s deep lack of knowledge on the subjects of crypto and jihadism.This report though made the rounds and ended up on places like NPR (which RF cited on their report LA DE DA) adding cache to it all.
Demonstrations/Tests
TorZillaPrint - arkenfox.github.io
Kloak - whonix.org
Kloak is a Keystroke Anonymization Tool.
Mouse Wheel Tracking Test - jcarlosnorte.com
Cover Your Tracks - EFF
Test your browser to see how well you are protected from tracking and fingerprinting
Studies
User re-authentication via mouse movements - dl.acm.org
We present an approach to user re-authentication based on the data collected from the computer’s mouse device. Our underlying hypothesis is that one can successfully model user behavior on the basis of user-invoked mouse movements. Our implemented system raises an alarm when the current behavior of user X, deviates sufficiently from learned “normal” behavior of user X. We apply a supervised learning method to discriminate among k users. Our empirical results for eleven users show that we can differentiate these individuals based on their mouse movement behavior with a false positive rate of 0.43% and a false negative rate of 1.75%. Nevertheless, we point out that analyzing mouse movements alone is not sufficient for a stand-alone user re-authentication system.
Feasibility of a Keystroke Timing Attack on Search Engines with Autocomplete (pdf) - vmonaco.com
Many websites induce the browser to send network traffic in response to user input events. This includes websites with autocomplete, a popular feature on search engines that anticipates the user’s query while they are typing. Websites with this functionality require HTTP requests to be made as the query input field changes, such as when the user presses a key. The browser responds to input events by generating network traffic to retrieve the search predictions. The traffic emitted by the client can expose the timings of keyboard input events which may lead to a keylogging side channel attack whereby the query is revealed through packet inter-arrival times. We investigate the feasibility of such an attack on several popular search engines by characterizing the behavior of each website and measuring information leakage at the network level. Three out of the five search engines we measure preserve the mutual information between keystrokes and timings to within 1% of what it is on the host. We describe the ways in which two search engines mitigate this vulnerability with minimal effects on usability.
What Are You Searching For? A Remote Keylogging Attack on Search Engine Autocomplete (pdf) - usenix.org
• Predict search queries using only client traffic
• Combine multiple independent weak predictors
• Escaped URL characters
• HTTP2 header compression
• Key-press time intervals
• Natural language
Hot or Not: Revealing Hidden Services by their Clock Skew - murdoch.is
Location-hidden services, as offered by anonymity systems such as Tor, allow servers to be operated under a pseudonym. As Tor is an overlay network, servers hosting hidden services are accessible both directly and over the anonymous channel. Traffic patterns through one channel have observable effects on the other, thus allowing a service’s pseudonymous identity and IP address to be linked. One proposed solution to this vulnerability is for Tor nodes to provide fixed quality of service to each connection, regardless of other traffic, thus reducing capacity but resisting such interference attacks. However, even if each connection does not influence the others, total throughput would still affect the load on the CPU, and thus its heat output. Unfortunately for anonymity, the result of temperature on clock skew can be remotely detected through observing timestamps. This attack works because existing abstract models of anonymitynetwork nodes do not take into account the inevitable imperfections of the hardware they run on. Furthermore, we suggest the same technique could be exploited as a classical covert channel and can even provide geolocation.
An Improved Clock-skew Measurement Technique for Revealing Hidden Services (pdf) - caia.swin.edu.au
SkewMask: Frustrating Clock Skew Fingerprinting Attempts - people.cs.umass.edu
In this work we present and implement a simple scheme by which a machine can mask, or intentionally misrepresent, its clock skew, as a defense against fingerprinting by remote machines. We demonstrate the manner in which this masking scheme can be used to disguise a single machine or a group of machines, and we explore the limitations of our masking defense.
General
Security and Privacy Advice - madaidans-insecurities.github.io
as titled
A Few Thoughts on Cryptographic Engineering - blog.cryptographyengineering.com
I’m going to devote this post to providing the world’s simplest explanation of why, in the threat model of your typical journalist, your desktop machine isn’t very safe. And specifically, why you’re safer using a modern mobile device — and particularly, an iOS device — than just about any other platform.
Despite DoH and ESNI, with OCSP, web activity is insecure and not private - blog.seanmcelroy.com
Certificate Transparency (CT) logs increasingly provide virtually every TLS certificate to be identified by serial number. Since OCSP responses are unencrypted and contain the serial number of the certificate as can be found in CT logs, as well as unsalted hashes of the certificate’s Distinguished Name and public key, these can easily be profiled to compromise the privacy of clients even in the presence of DoH and ESNI privacy protections.
Badness Enumeration - PrivSec.dev
Badness enumeration is the concept of making a list of known bad actors and attempting to block them. While it seems intuitive at first glance, badness enumeration should not be relied on for privacy or security. In many cases, it actually does the exact opposite and directly harms the user. This post will attempt to explain why badness enumeration as a concept is flawed and give some examples of its failings in practice.
The Six Dumbest Ideas in Computer Security - ranum.com
why are we spending all this time and money and still having problems?
Threat Modeling - privsec.dev
The first task a person should do when taking steps to protect their privacy and security is to make a threat model.
The right thing for the wrong reasons: FLOSS doesn’t imply security - seirdy.one
It’s no secret that I’m a passionate supporter of software freedom: I’ve written two posts about how Free, Libre, and Open-Source software (FLOSS) is necessary but insufficient to preserve user autonomy:
FLOSS Security - PrivSec.dev
While source code is critical for user autonomy, it isn’t required to evaluate software security or understand run-time behavior.
One of the biggest parts of the Free and Open Source Software definitions is the freedom to study a program and modify it; in other words, access to editable source code. I agree that such access is essential; however, far too many people support source availability for the wrong reasons. One such reason is that source code is necessary to have any degree of transparency into how a piece of software operates, and is therefore necessary to determine if it is at all secure or trustworthy.
Two types of privacy - seirdy.one
Threat modelling provides important context to security and privacy advice. Measures necessary to protect against an advanced threat are different from those effective against unsophisticated threats. Moreover, threats don’t always fall along a simple one-dimensional axis from “simple” to “advanced”.
Recovering redacted information from pixelated videos - positive.security
Information that has been redacted is often the most interesting. It’s therefore no wonder that some people might have a motivation to try to reverse such a redaction for various reasons.
In this blog post, I’ll discuss image/video blurring methods and their weaknesses and present a simple yet effective method to get a high-resolution image from a pixelated video in order to recover redacted information (with no guessing involved).
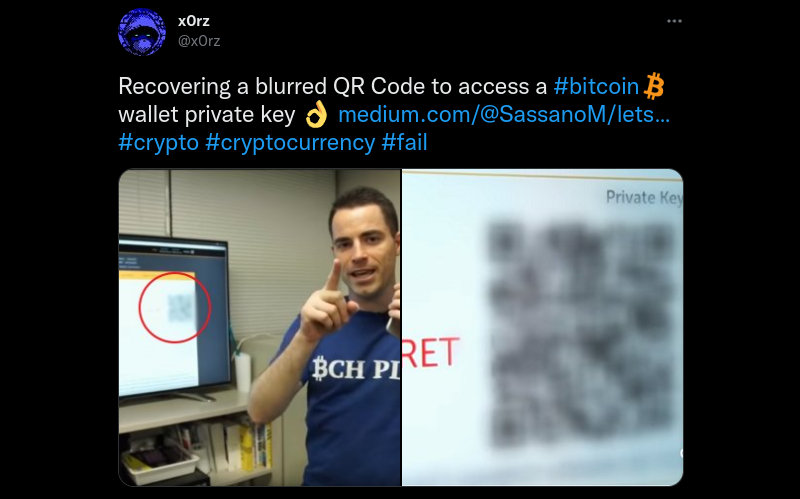
Let’s Enhance! How we found @rogerkver’s $1,000 wallet obfuscated private key - medium.com/free-code-camp
Last week France 2 broadcasted a documentary about Bitcoin. They interviewed @rogerkver who decided to offer $1000 in Bitcoin to the quickest viewer. Unfortunately, the QR code and the private key were obfuscated by France 2.
Wounded QR codes - datagenetics.com
QR codes store data in two dimensions in the form of an array of contrasting regions. The information density of a QR code is much higher than a vanilla barcode; depending on the format used and the resolution of reader, over a thousand bytes can be encoded in a region the size of a postage stamp.
QR codes use a Reed–Solomon error correction based technology to help recover from errors in reading (for instance, caused by a smudge, badly printed code or other deformity).
Tor, VPNs, also Fingerprinting
VPN - a Very Precarious Narrative - overengineer.dev
The popularity of those services and the way they are recommended and promoted is bad. So bad that I feel impelled to write this article on it, to explain two problematic points. Those are:
In most circumstances, VPNs do very little to enhance your data security or privacy unless paired with other changes.
Acting as they do, and promoting commercial VPN providers as a solution to potential issues does more harm than good.
Commercial VPN Use Cases - PrivSec.dev
Virtual Private Networks are a way of creating a protected and private network over the open Internet. It was originally designed to provide remote access to an internal corporate network. However, in recent years, it has also been used by commercial VPN companies to hide their clients’ real IP address from third-party websites and services.
Don’t use VPN services. - gist.github.com/joepie91
No, seriously, don’t. You’re probably reading this because you’ve asked what VPN service to use, and this is the answer.
Note: The content in this post does not apply to using VPN for their intended purpose; that is, as a virtual private (internal) network. It only applies to using it as a glorified proxy, which is what every third-party “VPN provider” does.
You want Tor Browser … not a VPN - matt.traudt.xyz
(in most cases) …Tor (thus Tor Browser) is in fact built correctly to disallow anyone from ever intercepting and reading the traffic between you and your guard relay. If your chosen VPN isn’t (good luck figuring it out), then Tor (Browser) is better. But honestly, your VPN is probably just as good.
IPVanish “No-Logging” VPN Led Homeland Security to Comcast User - torrentfreak.com
IPVanish, a VPN provider that for years claimed a strict no-logging policy, led Homeland Security to a suspect using a Comcast IP address, court papers filed in 2016 reveal.
h/t Packet Pusher.
I have more saved but thought this was getting a little long anyway. Could add some to this or publish a follow-up.