US Agencies Are Buying Your “Private” Internet Data
US Law enforcement agencies and military have been buying “petabytes” of American citizens’ internet data, according to a letter to the Office of the Inspector General.
According to a letter from Senator Ron Wyden (D-Oregon) to the Office of the Inspector General (OIG), the U.S. military and law enforcement agencies are buying up to ‘93% of the internet’ from the data broker Team Cymru.
The letter from Senator Wyden’s office:
I write to request that you investigate the Departments of Homeland Security (DHS), Defense (DOD) and Justice’s (DOJ) warrantless purchase and use of records revealing the websites Americans have accessed online.
For several years, I have been investigating the government’s purchase of Americans’ data, including location records and web browsing records. This investigation has confirmed that ‘multiple government agencies are purchasing Americans’ data without judicial authorization, including the Defense Intelligence Agency and Customs and Border Protection (CBP)–the latter of which is now being investigated for this practice by the DHS Inspector General.
While I have been able to make public important details about government agencies’ purchase of location data, my efforts to probe and shed light on the government’s purchase of internet browsing records have been frustrated by the Pentagon. On May 31, 2021, I wrote to the. Secretary of Defense to request that DOD provide me — without any restrictions on public release — written answers to questions regarding DOD’s purchase of Americans’ data. DOD had previously provided answers to my questions, which it marked Controlled Unclassified Information (CUI), on March 13, 2021. On August 2, 2021, the Under Secretary of Defense for Intelligence and Security responded to my written request, declining to remove the CUI restrictions on DOD’s answers to my question about intenet browsing records.
After DOD refused to release this information without restrictions, my staff learned that public contract information had been posted online, showing that multiple DoD agencies purchased data from data brokers that reveal internet browsing history: The Defense Counterintelligence and Security Agency spent more than $2 million purchasing access to netflow data, and the Defense Intelligence Agency purchased Domain Name System data. My office asked DOD to re-review their decision to maintain the CUI restrictions on the written answers DOD had previously provided, in light of these public contracts. DOD yet again refused, on May 25, 2022.
In addition, my office was recently contacted by a whistleblower who described a series of formal complaints they filed up and down their chain of command, as well as to the DOD Inspector General and the Defense Intelligence Agency, regarding the warrantless purchase and use of netflow data by the Naval Criminal Investigative Service (NCIS). According to the ‘whistleblower, NCIS is purchasing access to data, which includes netflow records and some ‘communications content, from Team Cymru,a data broker whose data sales I have previously investigated. Public contracting records also corroborate that NCIS has a contract for Augury, ‘which is the name of a subscription service offered by Team Cymru, which includes access to netflow data.
Public contracting records confirm that the Augury tool provides access to “petabytes” of network data “from over 550 collection points worldwide” and “is updated with at least 100 billion new records each day.” The contracting records also confirm that Augury provides access to email data (“IMAP/POP/SMTP peap data”) and data about web browser activity (“cookie usage,” “UserAgent data” and “URLs accessed”).
Contracting records state that the government contractor, Argonne Ridge Group, is the “only known source”of this data. Public records confirm that Team Cymru and Argonne Ridge Group have the same corporate address and have overlapping corporate officers. Government contracting records also confirm that in addition to NCIS, Argonne Ridge Group has contracts with U.S. Cyber Command, the Army, the Federal Bureau of Investigation and the U.S. Secret Service.
‘The whistleblower has informed my office that their complaint was forwarded by the DOD Inspector General to the Navy Inspector General. However, it appears from public contracting records that the government’s purchase of internet metadata, from just one data broker, goes far beyond the Navy. To that end, I request that your offices investigate the warrantless purchase and use of Americans’ internet browsing records by the agencies under your jurisdictions. Your independent oversight must ensure that the government’s surveillance activities are consistent with the Supreme Court’s Carpenter decision and safeguard Americans’ Fourth Amendment rights.
Here is the description of Augury included in the U.S. government procurement record:
The NAVSUP Fleet Logistics Center (FLC) Norfolk, Philadelphia Office intends to acquire, on an other than full and open competitive basis from Argonne Ridge Group, Inc., a subscription to Augury for fifteen (15) individually assigned accounts and data collection for 20 signatures in support of the Naval Criminal Investigative Service (NCIS), Quantico, VA. The subscription will provide for web-based access to an online repository of petabytes of current and historical network data to include BGP Origin ASN/BGP Peer ASN/BGP Prefix, DNS, NMAP scans, Pastebin archives, Botnet data, IMAP, POP, and STMP pcap data, RDP/FTP pcap data, and x509 Certs. The network data includes data from over 550 collection points worldwide, to include collection points in Europe, the Middle East, North/South America, Africa and Asia, and is updated with at least 100 billion new records each day. All IP addresses are geo-located with its domain and IP address ownership identified.
The service includes mapping IPv4 IP addresses to BGP prefixes and ASNs and is based on feeds from at least fifty BGP peers updated hourly. The tool provides the ability to identify a specific IP, an ASN (or ASNs), or an entire country to evaluate what routes have been announced or withdrawn, and by whom. Results are exportable in JSON, Excel, XML, and CSV file formats. The service also identifies compromised devices and botnet families based on network scanning activity and track malware infestations.
Data available includes:
- DNS history (forward and reverse)
- Operating system fingerprinting
- IRC keyword analysis
- NMAP scans
- Pastebin archived data
- Banners on networked devices
- Beaconing activity
- Cookie usage
- UserAgent data
- Extracted file information
- IMAP/POP/SMTP pcap data
- RDP/FTP pcap data
- URLs accessed
- x509 Certs
Senator Wyden found that U.S. law enforcement agencies are also buying access to Team Cymru’s tool. The FBI, the Secret Service, Border Patrol, etc. Enjoy your protection from unconstitutional search and seizure, lmao.
This site, cosive.com, used to describe the tool. The description has been replaced with “AUGURY HAS BEEN REPLACED BY PURE SIGNAL™ RECON Please note that Team Cymru Augury has been replaced by Team Cymru Pure Signal™ Recon.” However, an archived version of the website describes the tool.
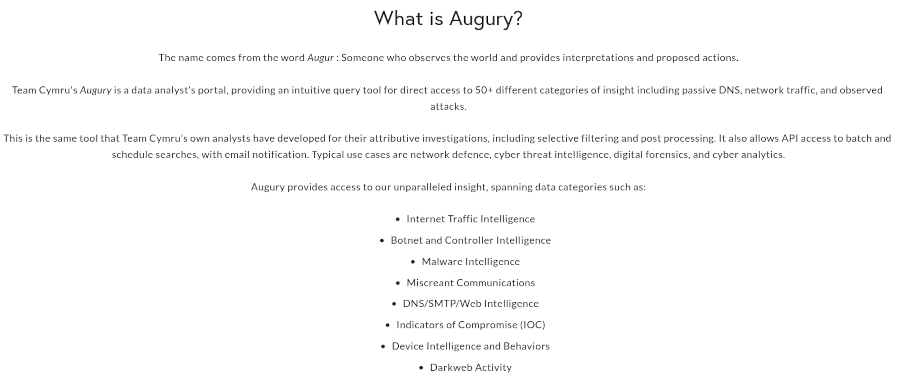
Team Cymru’s Augury is a data analyst’s portal, providing an intuitive query tool for direct access to 50+ different categories of insight, including passive DNS, network traffic, and observed attacks.
This is the same tool that Team Cymru’s own analysts have developed for their attributive investigations, including selective filtering and post processing. It also allows API access to batch and schedule searches, with email notification. Typical use cases are network defence, cyber threat intelligence, digital forensics, and cyber analytics.
Augury provides access to our unparalleled insight, spanning data categories such as:
- Internet Traffic Intelligence
- Botnet and Controller Intelligence
- Malware Intelligence
- Miscreant Communications
- DNS/SMTP/Web Intelligence
- Indicators of Compromise (IOC)
- Device Intelligence and Behaviors
- Darkweb Activity
And also:
AUGURY IS THE VISIBILITY INTO 93% OF INTERNET TRAFFIC
In a Motherboard article, Joseph Cox wrote:
The Augury platform makes a wide array of different types of internet data available to its users, according to online procurement records. These types of data include packet capture data (PCAP) related to email, remote desktop, and file sharing protocols. PCAP generally refers to a full capture of data, and encompasses very detailed information about network activity. PCAP data includes the request sent from one server to another, and the response from that server too.
How is this company getting PCAP data?