Encrypted eMail Company ProtonMail Denies Being Hacked
A recent paste on Pastebin claimed that hackers had hacked the encypted email service Protonmail. The so-called hackers provided no proof of the hack and the email service has responded, denying any hack had every ocurred.
In many cases, such immediate denials are categorically false. However, in Protonmail’s case, the denial has a decent chance of being correct. Although the message has raised concerns, the hackers provided no evidence to back up their claims and requested “a small fee” from the email company. If Protonmail refuses to pay, the hackers claim they will release user data to the world.
Many darkweb vendors use Protonmail for direct deals or communication with customers while a market is down. Although such compromisation should be a part of anyone’s threat model, Protonmail’s own inability to read encrypted emails prevents hackers from accessing the majority of sensitive information in the company’s possession.
Protonmail’s Denial
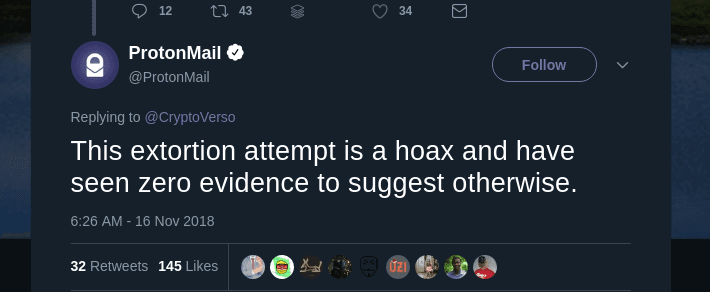
“This extortion attempt is a hoax and have seen zero evidence to suggest otherwise,” @Protonmail on Twitter wrote.
and
“We believe this extortion attempt is a hoax, and we have seen zero evidence to suggest otherwise. Not a single claim made is true and many of the claims are unsound from a technical standpoint,” their Reddit account added in a comment.
The Pastebin Claims
Source: Pastebin
Short Summary: We hacked Protonmail and have a significant amount of their data from the past few months. We are offering it back to Protonmail for a small fee, if they decline then we will publish or sell user data to the world.
Long Explanation: While Protonmail’s open-source code can be freely audited on Github, they haven’t configured the mandatory SRI feature (https://www.w3.org/TR/SRI/). This leaves users without any guarantee about their source code integrity, thus allowing tampering and data collection at anytime. This will be totally transparent and unnoticed, because without enabling SRI all the users should inspect the website runtime code and its connections manually in the same moment they’re being tampered with by Protonmail to discover it. Furthermore this requires spending a lot of time and advanced knowledge. With this being clarified, we have proven and recorded that Protonmail intentionally manipulated their source code to reveal users decryption keys (private keys) by collecting their password. Protonmail abuses the lack of SRI technology to serve a modified version of their code that allows full data collection and decryption of their users content. We haven’t found the exact pattern that triggers this (probably by targeting IP ranges or just randomly to collect everybody’s password), but again, we have proven and recorded this happens.
After proving Protonmail knowingly permits misconfiguration to maliciously target users we decided to deploy our full capabilities against them. We began with months of dedicated penetration testing, we asked assistance from other organizations and deployed unreleased 0-days. Although arduous we successfully installed a permanent backdoor on their major machines without Protonmail’s knowledge, bypassing their detection mechanisms. Once we obtained that access we took advantage of their misconfiguration and collected passwords from a large percentage of active accounts that accessed Protonmail during that period.
After that we were running a modified and automatized version of their webclient on our end, where we fetched, processed and stored email messages from those affected users in a huge database of our own, thus having significant useful information from many different individuals and companies.
If you have used Protonmail in the past several months it is probable we have your Username/Password and your decrypted emails recorded on our own private server. We also have names, addresses (If entered), contact lists, IP addresses, and much more. We would not have been able to do this if Protonmail did not deliberately mis-configure their code to harm their own users.
Incidentally during this period we noticed that Protonmail sends decrypted user data to American servers frequently. This may be due to the Swiss MLAT treaty requiring swiss companies reveal all their data to the Americans. However it also might be possible they are sending this decrypted user data to the American firm that owns them. This was simply a surprising thing to note but did not significantly influence our operation.
After we obtained significant user data from Protonmail we removed our permanent backdoor for our own security. However we will publish recordings showing our defeat of Protonmail’s defenses and using their intentional misconfiguration to tamper with their source-code.
We successfully fully compromised Protonmail and notified them privately of our operation. We also requested a small financial reward in return for their users data.
Protonmail compromises their users data without their knowledge and charges each user a monthly subscription fee. Therefore we felt morally justified compromising Protonmail’s data without their knowledge and charging them a fee for it’s return. We all worked hard to accomplish this, incurred costs and felt this was reasonable. However they declined and ignored further discussion. This seems to match their historical tendency to disparage researchers not at their own perceived high educational status.
After we send this email to the Media we again ask Protonmail to pay a small fee to have their user data returned to them. We have exposed their malfeasance to the world and the attention of their users is toward them. We will give Protonmail until 23 November at 12:00 UTC to pay the fee, guaranteeing safe deletion and exploit descriptions released to them in private. If given a choice we would not like to cause discomfort to regular people caught in this disagreement.
If they decline again we will distribute as indicated in both #1 and #2 below:
#1 Freely send media outlets the below information:
- -Data Group One: Decrypted emails between individuals working for private military contractors discussing government contracts. Specific details regarding circumventing the Geneva convention, underwater drone activities in the Pacific Ocean, and possible international treaty violations in Antarctica. We have no way to validate this information but we do have these users information and all the details they use when describing their activities to their acquaintances
- -Data Group Two: Conversations revealing rampant pedophilia among executives and the affluent who use Protonmail as their personal email. Including full names and descriptions of their wrongdoings in their own words. Prominent individuals to be named in many corporations and government positions.
#2 Sold in bulk to the highest bidder on the darknet:
- All decrypted Protonmail customer data collected during the period we compromised their source code. Including plain text emails, attachments, full names, social media connections and IP addresses. It’s possible we will not do this, instead selling email groups by topic.
Historically it seems Protonmail makes unkind statements toward upstanding organizations like my own. If this happens we will gladly release “data group two” to the general public.
In closing we wanted to express our desire to all Protonmail users that none of your data will be misused in any way if Protonmail cooperates. We understand that it may be difficult to gain peoples trust in this regard due to the manner in which we came into possession of their Data. All we can do is humbly offer our assurance that everything we have will be completely destroyed and never resurface again. It seems like in this age honor is dead however we will be honorable regarding this and our future actions will prove it.
Deadline 23 November 12:00 UTC
AmFearLiathMor
ADDITIONALLY FOR SALE:
1. Non-Disclosed 0-Days. We are happy to discuss sale, but we will not release them to you until after we are done dealing with protonmail
2. Our services and connections