Simple OPSEC Failure: Harvard Bomb Hoax
In 2013, a Harvard University student sent a bomb threat to university faculty members. Although the student had used the Tor Browser and an anonymous email address, law enforcement identified him hours after sending the threats.
I remembered this case after seeing a post by a user on Dread who asked about the “best way to safely hide tor usage.” Most people will probably remember this case.
The Bomb Threat
On December 16, 2013, “Eldo Kim, 20, of Cambridge, emailed several bomb threats to offices associated with Harvard University, including the Harvard University Police Department and the Harvard Crimson, the student-run daily newspaper.”
The emails had the subject line “bombs placed around campus” and contained the following message:
shrapnel bombs placed in:
science center
sever hall
emerson hall
thayer hall
2/4. guess correctly.
be quick for they will go off soon
a Harvard alert concerning the bomb hoax.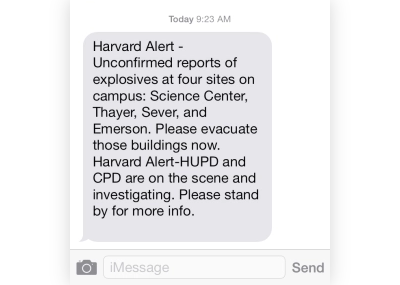
The Harvard University Police Department notified the Federal Bureau of Investigation (FBI) in response to the emails. The FBI immediately began an investigation on the campus, in coordination with the Bureau of Alcohol, Tobacco, Firearms, and Explosives (BATFE), the United States Secret Service (USSS), the Harvard University Police Department, the Cambridge Police Department, the Boston Police Department; and the Massachusetts State Police. Officers evacuated the buildings specified in the emails and searched them for explosives.
Police evacuated the listed buildings and searched for bombs
X-Originating-IP
The FBI investigated the origin of the emails. They learned that someone had used Guerrilla Mail, a disposable email service, to send the threats. Guerrilla Mail attaches the header X-Originating-IP:[the user’s IP address] to every outgoing email. The FBI saw that the person responsible for sending the emails had accessed Guerrilla Mail through Tor. The criminal complaint does not explain how the FBI learned that the suspect had used Tor. However, the simplest explanation is that Guerrilla Mail embedded the IP address of the Tor exit node Kim had used. As The Privacy Blog pointed out, “even if they had not embedded the IP, GuerrillaMail keep logs which would have been available to the FBI with a warrant.”
Guerrilla Mail is an anti-spam service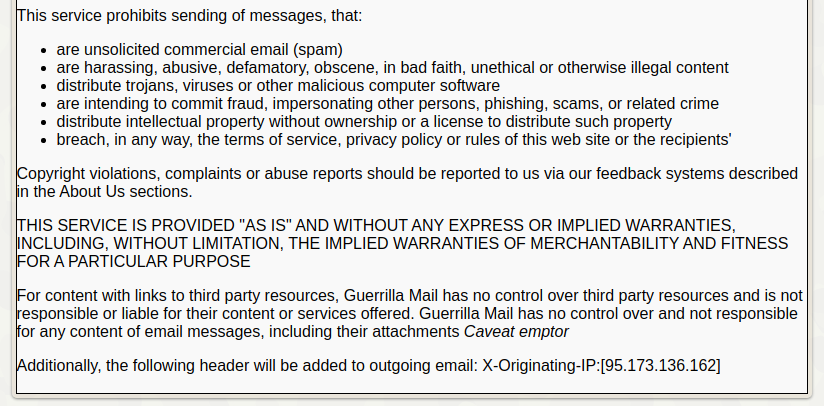
When investigating the IP address, the FBI saw that it matched an IP address of an exit node.
Investigators and Harvard University employees analyzed the logs for the University’s wireless network. The logs revealed that Kim had been using Tor in the hours leading up to receipt of the emails. The rest is history.
Confession
The FBI and an officer of the Harvard University Police Department questioned Kim. They advised Kim of his rights under Miranda. Then Kim confessed to sending the emails in an attempt to avoid taking an exam.
Kim then stated that he authored the bomb threat emails described above. Kim stated that he acted alone. He further stated that he sent the emails to “five or six Harvard University email addresses” that he picked randomly from the University’s web page. According to Kim, he was motivated by a desire to avoid a final exam scheduled to be held on December 16, 2013.
Kim further stated that he sent all of the threatening emails at about 8:30 a.m. and that he used TOR to create a “guerrillamail.com” email address for each of the emails. Kim explained that he sent all the bomb-threat emails from his MacBook Pro Laptop. Kim stated he chose the word “shrapnel” because it sounded more dangerous and wrote, “2/4. guess correctly,” so that it would take more time for the Harvard Police Department to clear the area.
Kim was scheduled to take a final exam in Emerson Hall, a building on the Harvard campus, at 9:00 a.m. on December 16, 2013. Kim stated that he was in Emerson Hall at 9:00 a.m. when the fire alarm sounded and the building was evacuated. According to Kim, upon hearing the alarm, he knew that his plan had worked.
To be clear, Tor did not fail. Kim was one of very few, if any, university students using Tor in time before the bomb threats were received.
Also, Kim’s plan was a success, I think.
Affidavit pdf
archive.org (DOJ Announcement)