Reminder: Facebook Helped the FBI Hack a Tor User
To help the FBI identify a Tor user in 2017, Facebook paid a cybersecurity firm to take advantage of a zero-day exploit in Tails, a privacy-focused operating system.
Buster Hernandez, known online as “Brian Kil,” notoriously coerced high school-aged girls to send him “child erotica” or sexually explicit pictures and videos. According to court records, Hernandez coerced these teenagers from about 2015 through mid-2017. However, during the FBI investigation (1:17-cr-00183) that resulted in his arrest, none of the victims were minors. The child pornography charges applied to content received through January 2016, indicating that his victims were perhaps 16 or 17 years old at the time. (Note: some news articles have different timelines than the criminal complaint but it appears as if his victims all stopped being minors long before the police arrested Hernandez. Additionally, he seemingly targeted high school-aged girls in general as some of them were not minors when he contacted them.)
Hernandez, through possibly hundreds of Facebook profiles created through Tor, sent messages to three teenage girls who went to a high school in Plainfield, Indiana. The messages generally followed a pattern outlined below:
“Brian Kil” contacted random individuals (typically minors) by sending private messages that said, for example, “Hi [Victim Name], I have to ask you something. Kinda important. How many guys have you sent dirty pics to cause I have some of you?” If the teenager responded, Hernandez would demand additional pictures or videos and threaten to distribute the ones in his possession if the girl refused to comply.
Brian Kil also just pretended to have explicit content altogether.
Hernandez became something of a problem for Facebook as well as the Plainfield community.
Hernandez was so notorious within Facebook that employees considered him the worst criminal to ever use the platform, two former employees told Motherboard. According to these sources, Facebook assigned a dedicated employee to track him for around two years and developed a new machine learning system designed to detect users creating new accounts and reaching out to kids in an attempt to exploit them. That system was able to detect Hernandez and tie different pseudonymous accounts and their respective victims to him, two former Facebook employees said.
Hernandez taunted Facebook employees, local law enforcement, and the FBI in some of his posts. Investigators never received anything but the I.P. addresses of Tor exit nodes when requesting information on “Brian Kil” from Facebook, email providers, and related services.
Brian Kil actually did better than most darkweb vendors as far as OPSEC goes.
So Facebook decided to hire a cybersecurity firm to help the FBI identify the user. They paid a cybersecurity consulting firm six figures to create a hacking tool that took advantage of a vulnerability in the video player that shipped with the Tails operating system. The cybersecurity firm’s tool, which they worked with a Facebook engineer to create, seemingly created a piece of malware disguised as a video file. When a Tails user attempted to view the video, the malware sent the user’s real I.P. address to a server controlled by the cybersecurity firm (or, at the end of the investigation, to a server controlled by alphabet boys).
Facebook gave the hacking tool to a third party who then passed it to the FBI.
In 2017, the FBI obtained authorization from a judge to deploy the Network Investigative Technique (NIT). The FBI described the file as a real video file with the malware attached to it.
Brian Kil seemed to believe the file or the DropBox account lacked content.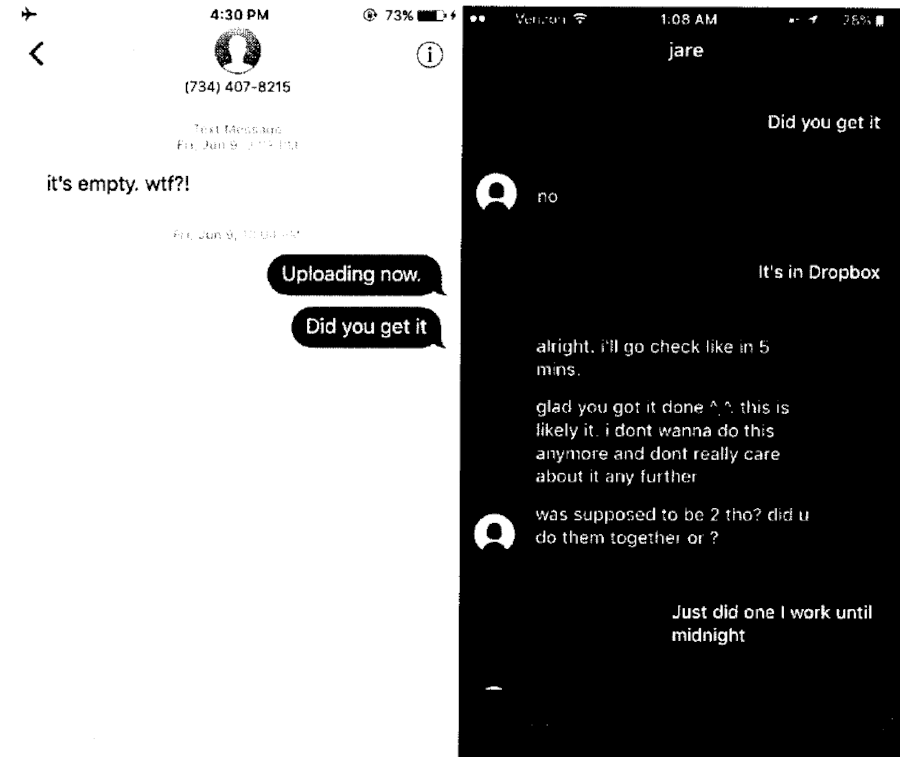
As outlined in the search warrant application presented to Judge Lynch, the FBI was authorized by the Court to add a small piece of code (NIT) to a normal video file produced by Victim 2, which did not contain any visual depictions of any minor engaged in sexually explicit activity. As authorized, the FBI then uploaded the video file containing the NIT to the Dropbox.com account known only to Kil and Victim 2. When Kil viewed the video containing the NIT on a computer, the NIT would disclose the true IP address associated with the computer used by Kil.
After obtaining the IP address, the FBI received authorization to install and use pen registers and tap-and-trace devices on the IP. The FBI, through the use of the wiretap, learned that Hernandez accessed Tor nodes after his significant other left the house. They also identified 4chan threads Hernandez had accessed, among other things.
Facebook sources told Motherboard that they justified their involvement in the creation of a hacking tool because of the type of crime Hernandez had committed. The defendant pleaded guilty to 41 charges, including Production of Child Pornography, Coercion and Enticement of a Minor, and Threats to Kill, Kidnap, and Injure. Additionally, Facebook employees said that an upcoming Tails release had removed the vulnerable code from the video player.
A Tails spokesperson told Motherboard that, at the time, they “didn’t know about the story of Hernandez until now and we are not aware of which vulnerability was used to deanonymize him.”
I am sure I will get inaccurately branded by the usual suspect as a defender of pedophiles or something for publishing this article. The fact of the matter is that if these companies are doing this to one person, they are doing it to others. Although Facebook’s six-figure Tails hack might be an extreme example, data uncovered in the BlueLeaks hack revealed that companies do this kind of stuff for free:
A little-known investigative unit inside search giant Google regularly forwarded detailed personal information on the company’s users to members of a counter-terrorist fusion center in California’s Bay Area, according to leaked documents reviewed by the Guardian.
[…]
Other users are identified by more sophisticated methods, and while some are banned from YouTube, they appear to retain access to other Google services.
One user was identified by matching two separate Gmail addresses to a single Android device, which yielded the user’s name, age, address, and phone number.
That user had posted YouTube comments making anti-Jewish comments, praising white supremacist terrorists, including mass killers, and suggesting he may emulate them.
I suppose that as long as you are buying packs of marijuana on darkweb drug markets and not doing a racism, you might be safe for now. The feds openly and almost regularly use NITs during child exploitation investigations. But given their explicit training on parallel construction and limitless resources, I doubt we know about even half of the cases in which an NIT was deployed against Tor users.
Criminal Complaint: pdf, html, html2
Also, I guess it is time for an article on the Rich Uncle Pennybags situation.
Also also, I tried to use archive.org instead of archive.is throughout. I personally like .is better as a service but the use of Google captchas is obviously a problem. Plus, have you ever tried logging into Dread?