Tutanota is Hardly the Solution to the ProtonMail Problem
Readers of Darknetlive, as well as users of Dread, have rightly recognized the risks associated with the use of ProtonMail. But the proposed alternatives are not without fault either.
Although ProtonMail is one of the few email providers that are not openly hostile to those who value their privacy, the company’s willingness to comply with law enforcement has concerned some users. To be fair, it is understandably difficult for me to criticize such a company when they do fight the majority of requests by law enforcement agencies. But when the company arbitrarily decided to comply with a request for information from law enforcement without a court order, they opened the door to unconditional criticism (most of which has been highlighted by commenters or various bloggers online).
Just drinking a cup of coffee. Normal OPSEC things.
One of the alternatives proposed by readers of this site is the email provider Tutanota. Tutanota provides some of the same features provided by ProtonMail but has many significant differences. Although both email services offer end-to-end encryption, Tutanota does not rely on PGP.
Oh, and there is that unavoidable javascript thing.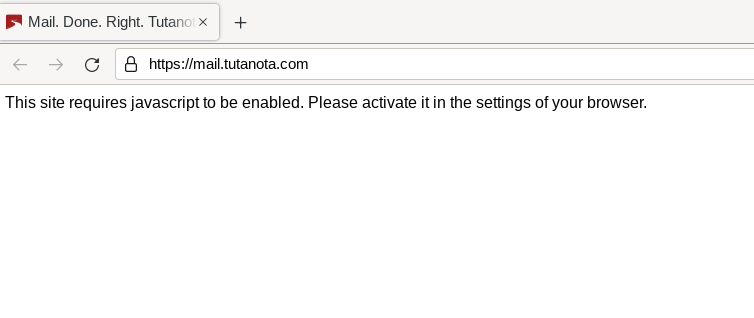
Tutanota uses standard algorithms also being used by PGP (AES 128 / RSA 2048) for encrypting the entire mailbox. Tutanota does not use an implementation of PGP because PGP lacks important requirements that we plan to achieve with Tutanota:
- PGP does not encrypt the subject line (already achieved in Tutanota),
- PGP algorithms can’t be easily updated,
- PGP has no option for Perfect Forward Secrecy.
A further description from one of the company’s FAQ pages:
For the email encryption between users, Tutanota uses a standardized, hybrid method consisting of a symmetrical and an asymmetrical algorithm. Tutanota uses AES with a length of 128 bit and RSA with 2048 bit. Emails to external recipients are encrypted symmetrically with AES 128 bit.
I suppose the consensus is that javascript is unavoidable when using a secure email provider that offers client-side encryption. As with ProtonMail, Tutanota is unusable with javascript disabled. Most security-conscious Tor users are then unable to access their inbox (without changing their security settings).
A complaint about ProtonMail is that the company makes it complicated to pay for services with cryptocurrrency. In fact, if you access the ProtonMail payment portal and select “Add Payment,” you are greeted with two choices: paying via credit card or PayPal. In order to use cryptocurrency (they only support Bitcoin), you have to select “Add Credits.” After adding credits, one can pay for ProtonMail services with the credts instead of the two payment options listed above. (Note: this is how ProtonMail used to work. It is possible that paying invoices with account credits is no longer an option.)
Tutanota, however, will gladly accept donations in the form of Bitcoin, Monero, Bitcoin Cash, Ethereum, PayPal, and Credit Cards. However, in order to actually pay for Tutanota services, users have only two options: credit cards or PayPal. Cryptocurrency payments is on the company’s roadmap. However, the company has been promising support for cryptocurrency payments since 2017. There have not been any updates to the issue on Github and it has been closed as “Off-Topic.”
ProtonMail provides what appears to be a false sense of security through their onion service. Naturally, it provides no function to Tor users with javascript disabled. Tutanota does not offer an onion service. Although it would likely be unusable if they did, they appear either dismissive or opposed to the idea. Although the company added support for an onion service to their roadmap, they marked the issue on Github “Off-Topic” and published a somewhat confusing blog post about how everyone should use Tor. The post seemed like the unveiling of a Tutanota onion service.
Oh, there it is on the roadmap. Right below support for emojis.
Does Tutanota log I.P. addresses? Well:
We only log IP addresses of individual accounts in case of serious criminal acts such as murder, child pornography, robbery, bomb threats and blackmail after being served a valid court order by a German judge. You can find details on this as well as on German data protection rights on our blog.
Which is effectively no different than ProtonMail’s logging policy. Tutanota apparently does not arbitraily decide to release information without a court order though. Or at least they have not admitted to doing so.
At the heart of the issue, though, is the company’s transparency report. After all, the recent stir about ProtonMail stemmed from an unfavorable update to their transparency report. To recap that incident, ProtonMail complied with a lawful court order that resulted in the arrest of a person identified by ProtonMail as a so-called “climate activist.” The form of activism, illegally occupying buildings, seems like homelessness with more steps. It seems equally bizarre that law enforcement agencies would devote the time and effort required to identify a ProtonMail user simply to arrest some totally-not-homeless person.
Here are the entries from the company’s transparency report for 2021:
Between the 1st of January 2021 and 30th of June 2021 Tutanota has
- received requests for inventory data in 109 cases.
- released inventory data in 6 cases.
- received requests for real time traffic data in 23 cases.
- released real time traffic data because of a German court order in 13 cases.
- received requests for stored content data in 32 cases.
- released stored encrypted content data because of a German court order in 21 cases.
- received requests for real time content data in 16 cases.
- released real time content data because of a German court order in 12 cases.
And for 2020:
Between the 1st of July 2020 and 31th of December 2020 Tutanota has
- received requests for inventory data in 92 cases.
- released inventory data in 2 cases.
- received requests for real time traffic data in 20 cases.
- released real time traffic data because of a German court order in 0 cases.
- received requests for stored content data in 37 cases.
- released stored encrypted content data because of a German court order in 34 cases.
- received requests for real time content data in 18 cases.
- released real time content data because of a German court order in 0 cases.
Between the 1st of January 2020 and 30th of June 2020 Tutanota has
- received requests for inventory data in 93 cases.
- released inventory data in 2 cases.
- received requests for real time traffic data in 5 cases.
- released real time traffic data because of a German court order in 0 cases.
- received requests for stored content data in 24 cases.
- released stored encrypted content data because of a German court order in 22 cases.
- received requests for real time content data in 5 cases.
- released real time content data because of a German court order in 0 cases.
It seems they released data more frequently in 2021 than in 2020. Tutanota provides entries for several periods of time on their transparency report.
At the end of the day, depending on threat models, people might need to operate as if nobody is trustworthy. And ultimatly, in this context, that statement is true. There are companies with what appear to be good track records such as Posteo. According to their transparency report, they only complied with one court order which was a mailbox seizure. Like any other email provider operating this way, Posteo is theoretically no different than ProtonMail or Tutanota when it comes to compliance with law enforcement. I have a suspicion that the people over at Elude have not complied with a single court order. I am not sure how law enforcement would serve one anyway. Please correct me if I am wrong on this count though.
P.S. I see people recommending Matrix as an alternative social networking/messaging platform. The Matrix.org foundation is suspicious at best as far as their metadata acquisition and retention policies go. Following their recommendations for setting up a self-hosted instance or using their recommended clients makes it very difficult to remove matrix.org and vector.im from the scenario.