Creating a PGP key pair #
When you create a PGP key pair, it gives you two unique keys: a public key, and a private key. You are to not, at any times, or for any reason, to give anyone your private key. That is for your eyes only. Your public key, however, is able to be given out so others can encrypt messages with your public key, send them to you, and then only YOU can decrypt them with your private key.
When you sign up to a market you may be asked to enter a public key. To prevent your market accounts from being linked together, you should always generate a new key pair for every account you make. Never upload the same public key to multiple accounts.
By uploading your public key you allow your vendor to securely send you sensitive information about your shipment (e.g. tracking codes). It can also serve as a two factor authentication mechanism to login to a market: every time you login you are required to decrypt a message containing a special code. Entering this special code proves that you own the account, because only you would be able to decrypt the message.
You should not keep private keys around that are no longer in use. If you make a new account on a market, delete the old key. If a markets gets busted or exit scams delete all keys for the accounts you created on that market. In the event that your private keys are compromised you want an attacker to be able to decrypt as little sensitive information as possible.
- create a new key first Open application->Accessories->Kleopatra
- File -> New Keypair
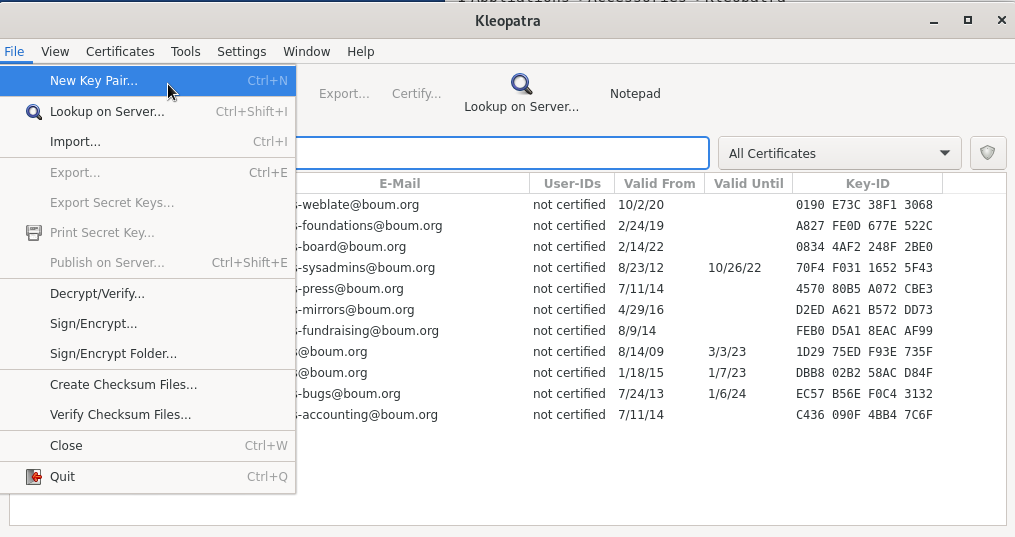
- Create personal OpenPGP keypair
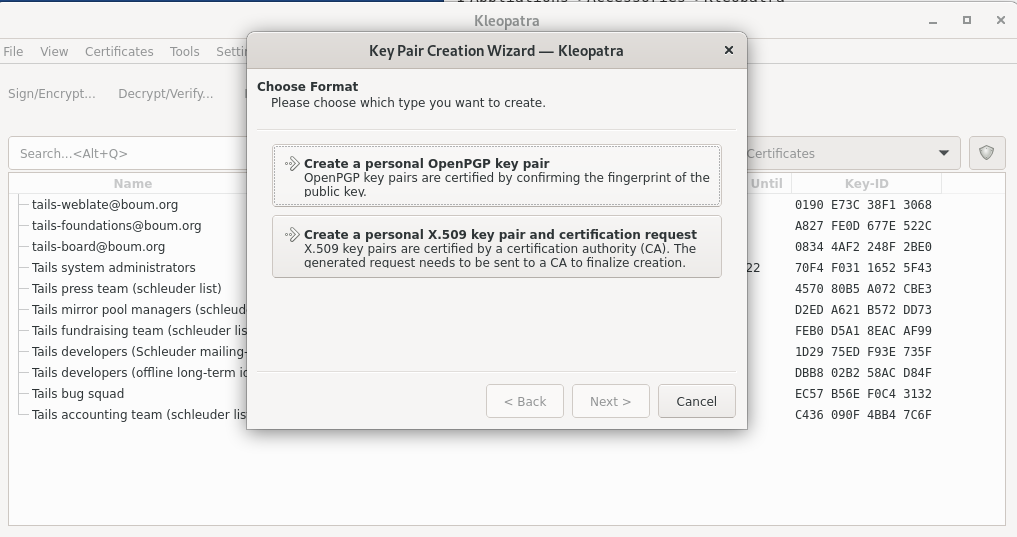
- Enter a name: Usually your account name for this key. Not your real name!
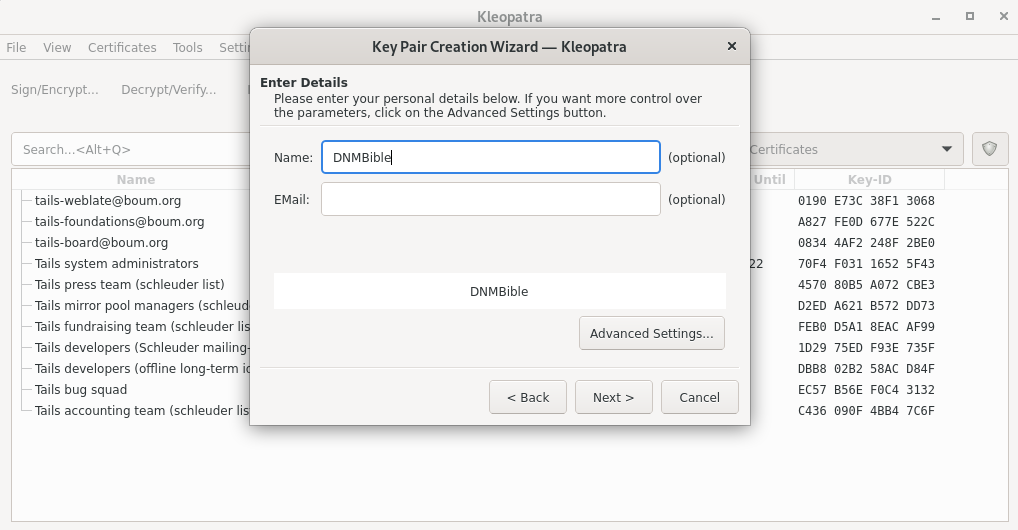
It is recommended to leave the email field blank. If you want to be contacted via email you can add one, but please make sure that it fulfills the recommendations mentioned in the email chapter.
- Advanced settings
- Change the 3072 bit options to 4096

- Set an expiration date to one or two years in the future.
Note: Setting an expiration date does not prevent messages that were encrypted with the associated public key from being decrypted in the future. In other words, if your private key is ever compromised an attacker can still decrypt messages after the key is expired.
The expiration date only serves as a reminder to periodically rotate your key pair, to limit the amount of sensitive information that can be decrypted with a single private key. When you do this be sure to let others know you are changing your key by signing your new public key with your old key.
Rotating a key only applies to keys that were created for off-market use. For example, a public key that you add to your profile on Dread. Keys created for market accounts are generally short-lived and should not be kept around for long.
- Click ok
- Next
- Create
- Enter a strong password
- You will now see a message box creating your keys. Once it is done you will see a notification letting you know it is finished.
Congratulations, you have now created your own PGP key pair!
Finding your public key
-
To find your public key double click the name of the key just created.
-
Click export
-
You should see something like this:
—–BEGIN PGP PUBLIC KEY BLOCK—–
Version: GnuPG v1
mQINBFhNDOsBEACzwJJVsMo7sIiLhvCsLx2n+DVHzw1trM/C8Yao8EmWdDYe3ei9 mXRqSudbD6S4KvJfm+ZeOlEQ6gGoG2q3aFYASRgcK7WDhs+jwG42EA+j2oIpU/EO 8EQXTmTn8T+LQT84JZ5KkiZZp2CqLU8RVszfkKEj1oX/sO5watxNQur4fbk9FiCA 1MjHMYir1g== =TV04 —–END PGP PUBLIC KEY BLOCK—–
You can now copy your key and send it to others to encrypt messages to you!
The gibberish part in the middle will be a bit longer though.
GNU privacy assistant only allows you to create keys that are 3072 bits, and lower. This is good security, but for best opsec practices you should be using 4096 bits. To do that we will generate the key in terminal.
Do all of the following steps on the Whonix Workstation.
Open a new terminal window and enter the following commands:
gpg --full-generate-key
1
4096
Select when you want your key to expire.
y
Enter a name for your new key. Make sure you don't use your real name! Or anything linked to you.
You can enter an email address if you want or you can skip it by pressing enter.
Enter a comment if you want or hit enter to skip
Review everything you just entered. If it looks good type o
A new window will open asking for you to create a password. This is where you can use KeePass to createcreate and store a new password for this set of keys.
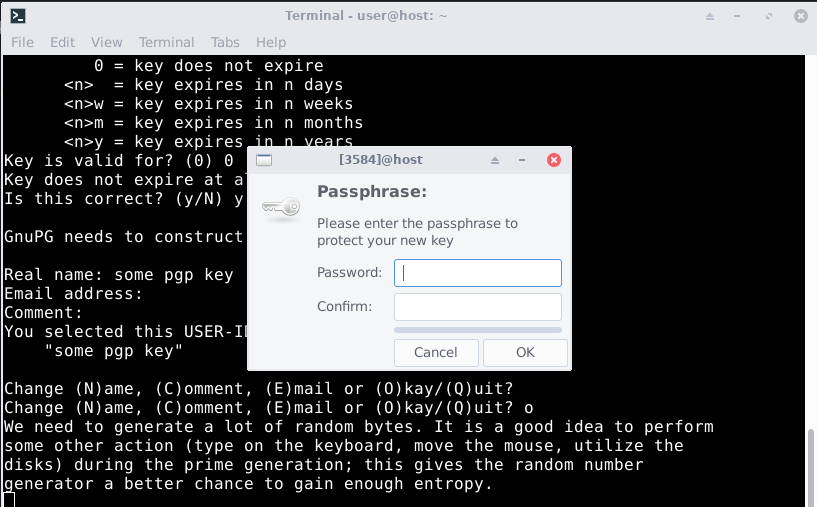
Once you enter your password move your mouse around. It will help create your new PGP key. You should now be able to open GNU Privacy Assistant and see your new key.
Congratulations, you now created your own PGP key pair!
One last thing: if you want to copy your public key, just right click on your key in the “Key Management” window (the one you see after opening GPA) Right click on your key. You will see an option to copy. This will copy your public key. You can now paste it where you need.
Your public key should look like this:
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: GnuPG v1
mQINBFhNDOsBEACzwJJVsMo7sIiLhvCsLx2n+DVHzw1trM/C8Yao8EmWdDYe3ei9
mXRqSudbD6S4KvJfm+ZeOlEQ6gGoG2q3aFYASRgcK7WDhs+jwG42EA+j2oIpU/EO
8EQXTmTn8T+LQT84JZ5KkiZZp2CqLU8RVszfkKEj1oX/sO5watxNQur4fbk9FiCA
1MjHMYir1g==
=TV04
-----END PGP PUBLIC KEY BLOCK-----
The gibberish part in the middle will be a bit longer though.
Note: Setting an expiration date does not prevent messages that were encrypted with the associated public key from being decrypted in the future.
It only serves as a reminder to periodically rotate your key pair, to limit the amount of sensitive information that can be decrypted with a single private key.